
ISO 27001 Implementation Steps: A Comprehensive Guide [2025]
![ISO 27001 Implementation Steps: A Comprehensive Guide [2025]](https://cdn.prod.website-files.com/6914eeceeacac851c05496eb/693818d1e4462bc2b623c186_692f5f59e9b7e4c3c81ef41d_6798af6c45a14d519c6c2e55_iso-27001-comprehensive-guide.avif)
Is your company looking at ISO 27001 certification in order to fortify your information security practices and bolster your reputation? If so, this comprehensive article will break down everything you need to know about this internationally acclaimed standard before you embark on the process of obtaining certification.
With companies processing more and more sensitive information in the current digital landscape, the importance of reducing risks, adhering to regulatory standards, and streamlining operations cannot be overlooked. As information security becomes increasingly critical, clients and organizations are becoming more unwilling to collaborate with companies that don’t hold their security infrastructure to the highest standards.
Achieving ISO 27001 certification demonstrates that your organization has incorporated a structured framework to mitigate cybersecurity threats and protect valuable information, ensuring confidentiality, integrity, and availability into its operations. By adhering to ISO 27001 standards, your organization will fulfill regulatory requirements, build trust with customers and partners, and enhance business resilience against disruptions.
Despite the myriad of benefits of ISO 27001 implementation and certification, it will demand a lot of effort and time on the part of you and your team. Keep reading for a step-by-step guide to key questions regarding implementing ISO 27001 standards and an Information Security Management System (ISMS).

I. Defining the scope of your ISMS
Early in the ISO 27001 process, your organization will have to define the scope of its ISMS. An ISMS is a systematic framework of policies, procedures, processes, and controls designed to manage your organization's information security risks. The ISMS is the core of ISO 27001. Its purpose is to protect the confidentiality, integrity, and availability of information by addressing threats, vulnerabilities, and compliance requirements.
In defining the scope of the ISMS, you’ll have to decide which information you need it to protect. You’ll also have to think about where that information is stored: Is it information stored physically in an office, whether in paper files or on computers? Is it stored in the cloud? Wherever the information is, if it’s within scope, you’ll be responsible for keeping it secure.
Establish What the Scope Includes
Defining the scope of your ISMS requires you to think critically about the various kinds of information your organization processes and stores, and the ways that it handles that information. A good place to start is with the scope requirements as outlined in ISO 27001.
As you establish the scope, you will define the context of your organization’s ISMS by considering internal and external issues, taking into account the needs and opinions of interested parties, and considering interfaces and dependencies between what is happening within the ISMS scope and the outside world. Then, you will need to identify and categorize your company’s relevant information assets. Lastly, it is crucial that your organization align the scope of the ISMS with its main business objectives.
At the end of your scope document, you should include a list of items that are excluded from the ISMS. If you decide to pursue ISO 27001 certification, your scope must be documented and readily accessible to auditors and organizational leadership. The auditor will check if all of the elements of the ISMS work well within your scope, but they will not check the departments or systems that cannot access the information that is covered by your scope. Adhering to an appropriate ISMS scope is key to fulfilling legal, regulatory, and contractual obligations.
Let’s break down the elements you will need to consider as you define the scope of your ISMS:

1) Define Organizational Context
Consider internal and external issues
Simply put, internal issues are factors that fall under the direct control of the organization, and external issues are factors your organization has no control over, but that it can anticipate and adapt to (defined in ISO 31000 clause 5.3.1).
Some examples of internal issues are:
- Governance
- Organizational structure
- Roles and accountabilities
- Policies, objectives, and strategy
- Capabilities
- Organizational culture
- Internal stakeholders
- Available resources
- Contractual relationships
Take time considering these internal components, as they will have a direct role in supporting your organization’s ISMS.
Some examples of external issues are:
- Market trends
- Values of interested parties
- Social factors
- Applicable laws and regulations
- Political and economic circumstances
- Environmental conditions
- Technology trends/innovations
ACTION: Make a list of the different internal and external issues that your company faces in order to fully understand the factors that could impact your ISMS.
TIP: Don’t forget to include external issues on the local, regional, national and international levels.
Take into account needs and expectations of interested parties
According to ISO 27001, interested parties are those individuals or groups that can influence, be affected by, or have an interest in the organization's information security. A good place to start is by identifying categories that these individuals/groups fit into: internal, external, or other.
For internal parties, a simple way to identify the interested parties within your scope is to ask the heads of departments at your organization about who is an important participant in their business operations. If your organization has a business plan, that is another way to identify individuals who may be interested parties in your ISMS.
Broadly, interested internal parties may be:
- Employees: Those employees responsible for handling sensitive data or using the organization’s IT infrastructure
- Executive Management: The leaders and decision-makers who are responsible for implementing risk management practices and strategies
- IT Team: Often the team responsible for implementing, maintaining, and protecting your organization’s technology and IT infrastructure
External interested parties are those outside of your organization that have the expectation that you will keep their information or their customers’ information secure. Other external parties may be those that have access to your organization’s information. In essence, it is likely that they could be impacted if your organization experiences an information security incident or breach.
External interested parties may include:
- Clients: Individuals or companies that rely on your organization to keep their information safe
- Suppliers and Contractors: Third parties or vendors that have access to information or process data on behalf of your organization
- Regulatory Bodies: Authorities that require your organization to comply with information security laws and regulations (e.g., GDPR, HIPAA).
- Investors or Shareholders: Those who invest financially in your organization and are concerned with the financial and reputational impacts of information security incidents.
- Business Partners: Businesses you collaborate with or share information with for business operations.
ACTION: For each interested party, document their specific information security requirements with regard to your organization, the risks associated with each party, and any legal or contractual obligations to each stakeholder.
TIP: As your organization evolves, the landscape of interested parties may change. Regular reviews should be conducted to ensure that new stakeholders are identified, and any changes in expectations or regulations are captured in your ISMS.
Consider interfaces and dependencies between what is happening within the ISMS scope and the outside world
In the context of your ISMS, interfaces and dependencies refer to the interconnected systems, processes, and external relationships that influence your organization’s security posture.
- Interfaces can be defined as the points of interaction between your company's ISMS and external or internal systems, processes, or parties. An easy way to identify interfaces is to think about all of the endpoints that are within your organization’s control. This could include:
a) Internal interfaces: the interactions between different departments, systems, or processes within your organizatio
b) External interfaces: interactions with external stakeholders such as customers, suppliers, cloud providers, or partners. If a vendor handles sensitive data or IT infrastructure, these interfaces must be considered within the scope.
In the context of ISO 27001, defining the interfaces helps ensure that all touchpoints where data and information are exchanged, whether internally or externally, are secured under the ISMS. Examples include API connections between systems, vendor management systems, and even service agreements with external providers.
- Dependencies are the external or internal resources that an organization relies on that are critical for the ISMS's proper functioning. This could be in terms of hardware, software, third-party services, or people. Dependencies often include:
a) Technological Dependencies: Examples of these are external cloud services, cybersecurity software, and even specific IT infrastructure.
b) Supplier Dependencies: This could be a third-party hardware maintenance company that services your organization's physical IT infrastructure, such as servers, network devices, or storage systems.
c) Human Resource Dependencies: This includes key personnel or teams responsible for maintaining security practices or handling sensitive information.
Understanding the interfaces and dependencies within your ISMS scope will allow you to implement appropriate controls throughout the ISO 27001 process so that security measures extend across all touchpoints, safeguarding both internal data and external integrations.
ACTION: For interfaces, list out each endpoint that your organization controls (internally and externally). For dependencies, make a list of each internal and external resource that your organization relies upon for the ISMS’s proper functioning. (Technological, Supplier, Human Resources, etc).
2) Identify Relevant Assets
Within the scope of your ISMS, you’ll need to identify and categorize the assets that the ISMS aims to protect. Again, an effective jumping-off point is to create categories for the types of assets that will be covered in the scope of your ISMS.
- Information Assets: These are the most critical assets in the ISMS, such as customer data, employee information, intellectual property, business processes and records, and documentation.
- Physical Assets: You’ll also need to consider the physical assets that store, process and protect information. They are tangible items like servers, workstations, network equipment, data centers, storage media, and other office equipment.
- Software Assets: These are all the programs, applications, and systems that your organization relies on to manage information, including operating systems, enterprise applications, security tools, and any cloud-based services.
- Personnel Assets: Instilling an awareness and dedication to security among personnel is crucial for implementing a successful ISMS. Personnel assets could be employees, contractors, system administrators, and external consultants.
- Third-party Assets: Your ISMS may include assets that are owned or managed by your organization’s third-party vendors, like vendor systems, outsourced services, and supplier systems.
ACTION: Make a list of assets for each of the categories above. By categorizing the assets that will be covered within your ISMS, you can facilitate the rest of the ISO 27001 process, as this initial categorization will help you more easily identify risks and implement controls.
TIP: Other categories like intangible, organizational, and environmental assets can be used depending on how detailed and specific you need your ISMS to be.
3) Align Your Scope and Business Objectives
As you create the scope of your ISMS, it is essential to make sure that it aligns with the core mission and objectives of your company. To do so, you will need to have a clear understanding of how information security supports your organization.
Define Key Objectives
What is your organization’s main priority in pursuing ISO 27001 certification? Are you most concerned about protecting customer data, maintaining operational continuity, or complying with laws and regulations? Certainly, each of these aspects is critically important, but it is crucial to identify the driving force behind your pursuit of ISO 27001 so that you can optimize the protections and controls that are the most relevant to your organization’s goals. Once you have figured out these core objectives, you can ensure the ISMS scope covers all critical areas that may affect them, including relevant departments, processes, and information assets.
Assess Risks & Prioritize
Once you’ve established core business objectives, you can assess your organization’s tolerance for risk and prioritize the assets within scope by order of importance with regards to your business goals. If a core tenant of your company’s mission is innovation, for example, intellectual property protection should be central to your ISMS. Don’t forget that the scope also must include the third-party relationships, technology, and physical infrastructure that are essential to your business operations.
Aligning the scope of your ISMS with your company’s core objectives will demonstrate how information security supports the growth, reputation, and compliance of your business, which will allow your organization to achieve security and business goals simultaneously.
ACTION: Organize a meeting with key stakeholders, including executives, department heads, IT leaders, and compliance officers, to define and align the ISMS scope with your organization’s objectives. In the meeting, clarify business priorities, map objectives to information assets, discuss risks and dependencies, and don’t forget to document your discussion.
Practical Steps to Defining Your Scope
When considering what your ISMS scope should include, it’s important to reference guidelines on scoping documentation, consult with key stakeholders, and research common challenges to avoid.
Compile Scoping Documentation
As stated above, your scope will include a document comprised of the following elements:
- A Scope Statement: Defines the boundaries of the ISMS in terms of what is included and excluded.
- Context of the Organization: Details internal and external factors affecting the organization’s ability to achieve ISO 27001 objectives
- Interested Parties and Their Requirements: Defines the ISMS key interested parties and their requirements, as well as which of these requirements will be addressed in the ISMS
- Interfaces and Dependencies: Lists internal systems/teams and external organizations that are critical to your operations and how risks associated with them are being managed.
- Information Asset Inventory: Detailed list of all information assets within the defined scope of the ISMS
Other documentation that will assist your company throughout the process of establishing your scope include:
- Risk assessment and treatment documentation
- Organizational structure diagram
- Process and workflow documentation
- Network architecture diagram
- Regulatory and legal documentation
- Third-party and supplier documentation
These scoping documents collectively help define the boundaries of the ISMS, ensuring that the system is manageable, clearly defined, and properly aligned with business objectives and security needs.
Consult with Key Stakeholders
Because ISO 27001 certification can be a labor-intensive process, it is important that key stakeholders support your company’s effort so that you can get the process off of the ground. Considering key stakeholders when defining your ISMS is crucial for aligning it with business objectives, identifying and prioritizing risks, and affirming regulatory compliance. Stakeholders, such as senior management and department heads, provide vital insights that help tailor security controls, allocate resources, and support decision-making. Their involvement builds organizational buy-in and ensures that the ISMS addresses the specific needs of different departments. In addition, stakeholders can help identify external dependencies, enabling the ISMS to continuously improve and adapt to evolving risks, which promotes long-term sustainability and resilience. Engaging them leads to a more effective and comprehensive ISMS.
What to Avoid When Planning Your Scope
When planning the scope of your organization’s ISMS, there are a few common pitfalls that you should be aware of:
Defining Too Broad or Too Narrow a Scope
Trying to include too many elements in the scope of your ISMS can overwhelm your allocated resources, while a scope that is too narrow may miss key areas of risk. Consulting with an expert on ISO 27001 certification, like BD Emerson, is a great way to ensure that your scope is focused but comprehensive.
Leaving out Key Stakeholders
One of the most important elements of a successful ISMS scope is including the right stakeholders from the get-go. Failing to engage departments like IT, legal, and senior management can cause misalignment with business goals and inadequate risk management. It can also cause confusion and a lack of clear communication among teams, which can be detrimental to the success of your ISMS and achieving ISO 27001 certification.
Overlooking Legal and Regulatory Requirements
When defining your scope, it is crucial to research and list out all of the legal and regulatory requirements that your organization may be subject to. Failing to do your due diligence could result in legal penalties and non-compliance. This is also an area where your organization may have opportunities for compliance with other key information or data security frameworks. For example, many of ISO 27001’s requirements overlap with GDPR (General Data Protection Regulation). If your business plans to pursue work in the European Union, it will have to be GDPR compliant. Fortunately, ISO 27001’s requirements satisfy some of GDPR’s standards, so you would not have to duplicate your efforts.
Excluding Critical Information Assets
It is critical to be as thorough as possible when defining your organization’s information assets in your ISMS scope. Forgetting to include essential data, systems, or processes exposes the organization to security risks.
Inadequate Resource Planning
Many organizations make the mistake of underestimating the time, resources, and funds it can take to achieve ISO 27001 certification. Not allocating sufficient budget, personnel, or technology can lead to gaps in security and an incomplete implementation. As you define the scope of your ISMS, it is important to consider your organization’s capabilities and resources.
II. Building Out Real Risk Management Functionality
Once you’ve established the scope of your ISMS, you’ll need to get into actually implementing ISO 27001 standards by performing a risk assessment and implementing controls. ISO 27001 follows a risk-based management approach, meaning that identifying risks to information security is a key factor in choosing which controls need to be implemented into your organization’s security infrastructure.
The scope you created for your ISMS will be extremely useful in helping your organization identify risks because you have already listed many of them within the scope itself. ISO 27001 clause 6.1.2(c)(1) specifically relates to the process of identifying risks as part of the risk assessment activity required for an ISMS. This clause requires organizations to identify risks to the confidentiality, integrity, and availability of information that could arise from potential threats and vulnerabilities.
Risk Assessment Methodology
Before you begin your risk assessment, you’ll need to define your risk management methodology. The purpose of this methodology is to establish best practices for identifying, assessing, and treating/mitigating risks. It is also how you will define an acceptable level of risk for your organization. A common mistake companies make is to begin the risk assessment without laying out clear rules for it.
ISO 27001 clause 6.1.2(c)(1) requires the following elements to be included in your risk assessment:
1) Define how to identify the risks that could cause the loss of confidentiality, integrity, and/or availability of your information
Use the list of assets that you’ve included in your scope in order to identify risks. ISO 27001 also has a Catalog of Threats & Vulnerabilities to which you can refer. Once you have a detailed list, you will assign risks and risk levels to each of them. Think of risks as anything that could impact the confidentiality, integrity, and availability of each listed information asset. Examples of risks include unauthorized access to databases, incidents of fraud or corporate espionage, insufficient data backups, or poor password management practices, etc.
2) Define how to identify the risk owners
In order to assign risk owners to each risk, you need to consider who will be in charge of managing a given risk. First, map out the business functions that are impacted by these risks, then determine who the individuals or teams are that have control over the area in which the risk exists. Risk owners should have decision-making authority with regards to how the risk is managed.
3) Define the criteria for assessing consequences and assessing the likelihood of the risk
Because ISO 27001 does not require a specific way to measure risks, your organization will need to create its own way of analyzing and scoring risks. As stated above, it is crucial to create a standard approach for the entire organization so that the results of the assessment are consistent.
4) Define how the risk will be calculated.
A common method of calculating risk is to create a risk matrix that outputs a risk score. This can be an effective method that is easily repeated for each risk.
Follow these steps to create a score for each risk:
a) Determine Likelihood
Once you have decided on an approach, you will need to assign levels of risk by assessing the likelihood of a risk occurring as well as the potential impact it could have on your organization. In determining the likelihood of a risk occurring, you must consider historical data on similar incidents, vulnerabilities in existing systems, and the frequency of threats or attacks. Typically, you assign risk levels to each risk from 1 (very low likelihood) to 10 (very high likelihood).
b) Evaluate Impact
Once you have established the probability of an incident occurring for each risk, you can move to assess the potential impact of a risk if it were to happen. This is also scored from 1 (very low impact) to 10 (catastrophic impact). To determine the impact score, consider possible financial loss, the effects on operations or service delivery, reputational or legal damage, and harm to the confidentiality, integrity, and availability of information.
c) Calculate the Risk Score & Categorize Risks
Multiply the likelihood and impact scores for each risk to calculate a total risk score. This will give you a score between 1 and 100. The higher the score, the more severe the risk. Once you have your risk scores, categorize them into high-risk, medium-risk, and low-risk categories.
5) Define the criteria for accepting risks.
Once you have calculated the levels of risk for the risks you’ve identified, establish your organization’s risk tolerance or acceptable risk levels. This defines the threshold above which risks need to be mitigated.
For example, you may decide that risks with a score above 50 might be deemed unacceptable and require immediate action, while risks below that threshold are permissible as long as they are monitored, but do not require active mitigation.
Whatever method your organization chooses for calculating and assigning risk, then determining an acceptable level of risk, you will need to ensure that you can apply these requirements and criteria to each risk assessment performed across your organization so that every assessment achieves measurable and comparable results.
It is important to adopt a risk assessment methodology that fits appropriately to your business objectives. Choosing a methodology that doesn’t reflect your company’s values or mission can result in a longer, more disorganized process.
As you establish your risk assessment methodology, consider using tools that can help you simplify the process while staying on track. Automated tools like Vanta support custom frameworks that allow organizations to tailor their risk assessment and management processes to their unique business context, which aligns perfectly with ISO 27001’s risk-based approach.
Creating a Risk Assessment Methodology - Summary
Once you have established your risk methodology, you are ready to perform an information security risk assessment for your organization. As explained above, keep in mind that your information security risk assessment must perform four key functions:
a) establish and maintain information security risk criteria that include risk acceptance criteria and criteria for performing information security risk assessments
b) ensure that repeated information security risk assessments produce consistent, valid, and comparable results
c) identify information security risks associated with loss of confidentiality, integrity and availability of information within the scope of the ISMS along with the risk owners
d) analyze the information security risks and assess the potential consequences and realistic likelihood of the following risks occurring: cyber threats, human error, insider threats, system failures, third-party risks, and physical threats.
e) evaluate the information security risks and compare the results of the risk assessment with the risk criteria established in ISO 27001 clause 6.1.2 (a), then prioritize the analyzed risks for risk treatment.
This assessment, like all parts of the ISO 27001 implementation process, will need to be thoroughly documented.
Performing the Risk Assessment
Now, it’s time to perform the risk assessment. You will need to collect a large volume of information from each department of your organization.
It’s important to be strategic about how you plan to collect this information. How much time do you have to devote to information collection? Can you afford to have employees temporarily pivot from daily tasks in order to complete risk assessment interviews/documents, or will you need to invest in a training/workshop provided by a consultant/third-party risk assessment training provider to get it done?
You will also have to think about how you will get this information in the most thorough and efficient way possible.
Some sources of information about your organization’s risks may be:
1) Interviews with Stakeholders
Performing comprehensive interviews with those responsible for your organization’s sensitive data and security practices is the best way to collect key information about possible risks and opportunities.
2) Questionnaires
Requiring a broad selection of employees to complete a structured questionnaire that includes questions about their awareness of information security practices, perceived risks, and their interactions with IT systems is another way to collect information for your risk assessment. While this method can provide valuable insights, it is not always the best way to collect high-quality information, as many times employees do not want to prioritize completing a lengthy questionnaire over actually getting work done. If this method is used, it is best to employ it in tandem with other information collection strategies.
3) Document Review
When collecting information about possible risks, don’t forget to review your organization’s current information security policies, procedures, guidelines, and any documented business processes to understand the company’s expectations regarding how information is being managed and protected. In addition, if your organization has already completed other risk assessments, audits, and compliance documents in the past, you should review those documents along with any audit reports in order to better understand areas of vulnerability and risk that have already been identified.
4) Asset Inventory
Performing an asset inventory is something you have most likely completed while defining the scope of your ISMS as mentioned in the last section. Gather data on all assets (e.g., hardware, software, databases, and information repositories) that are critical to your organization. This information will give you a better idea of the location of certain risks to your organization. Throughout this process, you’ll need to engage with the owners of these assets to better understand their importance, usage, and potential threats.
5) Technical Testing
Performing a risk assessment can be an overwhelming process, but it doesn’t have to be. Employing software, automated tools, and/or working with external information security experts can alleviate the burden of collecting certain types of information manually.
Some processes that can be performed by automated tools or third-party consultants like BD Emerson include:
- Vulnerability Scanning: A scan of the organization’s network, systems, and applications for known vulnerabilities
- Penetration Testing: Simulating cyber attacks on your systems, pentesting exposes exploitable weaknesses in your organization’s systems and networks.
- Log Analysis: Review of system and application logs to detect unusual or suspicious activities
Learn more about BD Emerson’s Technical Services
6) Incident and Event History Reviews
Analyze past incidents and security reports (e.g., data breaches, malware infections, or unauthorized access events) and note vulnerabilities that have already been exploited. Consult Help Desk or IT support logs to identify recurring technical issues that may indicate weaknesses or areas of concern.
7) Supplier and Third-Party Assessment
Communicate with your vendors or third-party service providers to gather data on their security posture. This can include reviewing SLAs, security certifications, and audit reports. You should also evaluate the processes associated with your supply chain. Don’t forget to examine the security measures of any outsourced IT services or cloud storage providers your organization works with.
8) Workshop/Brainstorm Sessions
An effective way to gather information across departments may be to facilitate a workshop/brainstorming session with the participation of critical stakeholders to expose potential risks, discuss threat scenarios, and consider the likelihood and impacts of those threats. This can also be effective in providing time for employees and stakeholders to step away from their daily tasks in order to focus wholeheartedly on analyzing your organization’s security posture.
9) Analysis of Compliance and Legal Requirements
Review the legal, regulatory, and contractual requirements on your organization’s information security to better understand external risks linked to non-compliance. Compare your organization’s security practices to relevant industry standards such as NIST and other frameworks.
10) Business Impact Analysis
To inform your risk assessment, you should have a thorough understanding of how heavily your organization relies upon the functioning of its information security systems and technology. Evaluate the potential financial, operational, and reputational impact of security incidents through data on past downtimes and recovery costs. How vulnerable is your organization overall in the face of potentially disruptive and devastating information security and cyber threats?
11) Gap Analysis
Inevitably, while conducting your risk assessment, you will need to compare your organization’s current information security controls against those required by ISO 27001 to identify any gaps or weaknesses. Assess the maturity of your organization’s information security practices to understand how well current measures are implemented and where improvements can be made.
Tackling Information Security Risk Treatment
Once you have completed your organization’s information security risk assessment by collecting key information, calculating risk scores, and assigning risk levels, you can move on to tackling risk treatment. While a risk assessment can be one of the most complex parts of the ISO 27001 implementation processes, risk treatment can be one of the most costly and requires a strategic approach.
Risk treatment entails modifying a risk by changing its likelihood and/or impact. The main purpose of risk treatment is to control and address the risks identified throughout the risk assessment. While it is important to consider all risks to your organization’s information security, it is vital to focus your risk treatment efforts on the risks you have identified as unacceptable, or else the process could become too costly and unfocused.
As you establish your security risk treatment process, make sure that it:
a) takes into account the risk assessment results
d) determines all necessary controls for implementation of the information security treatment option(s) chosen;
c) compares the controls necessary to implement information security risk treatment options chosen by your organization
d) compares the identified controls with Annex A (in scope document) to ensure no controls are omitted
e) Produces a Statement of Applicability (SOA)
Once you have compiled a list of unacceptable risks, you should decide how to treat each one individually.
Risk Treatment Options
When it comes to risk treatment, there are four main options that are the most common:
1) Decrease Risk
This is the most common approach to treating the many risks that companies face. As you navigate ISO 27001 standards, you will need to either implement new controls or prove that you have them in place already, and that they are effectively reducing the likelihood and impact of the given risks.
Example: In this scenario, there is a high risk of a data breach occurring from phishing attacks. To lower the likelihood and impact of this risk occurring, the company in question will implement a risk reduction strategy that includes the following controls from Annex A of ISO 27001:
A.7.2.2 Information security awareness, education, and training - Roll out a robust security awareness training program to teach employees and personnel how to recognize phishing emails, engage in safe email practices, and how to act if they receive a suspicious email. This solution decreases the likelihood that employees will fall for phishing attacks by improving their ability to recognize threats and respond appropriately.
A.9.2.2 User access management - Implementing two-factor authentication (2FA) for access to all critical systems and sensitive data will protect systems from phishing attacks even if a phishing attack successfully captures an employee's password. 2FA means the attacker would still need the second authentication factor (e.g., a code sent to a mobile device) to successfully log into the system. This control limits the impact of a phishing attack because, though password/login credentials have been compromised, the attacker cannot actually access company systems.
A.12.6.1 Management of technical vulnerabilities - Ensuring that all software is up-to-date with the latest security patches, particularly email clients and web browsers that might be used to access malicious links reduces the likelihood of employees’ devices being compromised by vulnerabilities exploited through phishing.
A.16.1.5 Response to information security incidents - Developing and regularly testing an incident response plan that includes procedures for responding to phishing attacks can minimize the impact of a breach by ensuring that fast action is taken to prevent the spread of an attack. This control includes immediate containment, investigation, and notification to stakeholders.
2) Avoid Risk
When it comes to risks that are simply too threatening to mitigate with other options, your organization may choose to halt certain processes or tasks altogether.
An example of this could be stopping the usage of outdated legacy systems that can no longer be patched or updated to address security vulnerabilities. Systems that can’t be updated to prevent risks are vulnerable to attackers and can lead to devastating data breaches. If your organization wants to minimize risk, discontinuing the use of legacy systems altogether and instead replacing them with modern and secure alternatives can eliminate the vulnerabilities inherent in the use of the older systems.
3) Share Risk
Sharing risk is also known as risk transfer and involves the shifting of responsibility for managing a risk to another party. This is commonly done through mechanisms such as insurance, outsourcing, or using third-party services. If you opt for any sort of insurance related to an information security risk, your company still retains some responsibility, but this arrangement mitigates the potential impact by transferring part of the risk to another entity.
If your company operates in a high-risk industry like health care, it may have a much higher likelihood of experiencing a data breach. Knowing a data breach could result in significant financial costs due to fines, legal fees, customer compensation, loss of business, and reputational damage, you might want to consider cybersecurity insurance. Your organization still needs to implement reasonable security controls and respond to breaches, but you will have transferred a significant portion of the financial risk to an insurance company.
4) Retain/Accept Risk
Accepting risk is when an entity chooses not to take any further action to mitigate, avoid, or transfer a risk because the potential impact is deemed acceptable, or the cost of mitigating the risk outweighs the benefit. Before deciding to retain a risk, you should perform a cost-benefit analysis on what it would cost and involve maintaining a risk or reducing/avoiding it.
An example of choosing to retain a risk might be as simple as choosing to maintain your company’s website because the benefits it offers–providing information and a point of contact for your organization–significantly outweighs the occasional downtime your website might experience due to server maintenance or unexpected technical issues. This is a potential risk that your company can prepare for, however, and respond to it when it occurs.
Integrating Risk Management into Day-to-Day Operations
Effective risk management is not a one-time thing, cyber threats and other risks are constantly evolving, meaning that your security risk management strategy has to evolve with them and become a key part of your day-to-day operations.
Here are three strategies:
- Support a Culture of Risk Awareness Among Employees and Partners - Building a culture of risk awareness starts with ensuring all employees, from entry-level to executives, understand their roles in safeguarding information assets in your company. Communicate clearly to your employees regarding the importance of identifying and addressing cybersecurity threats as quickly as possible in order to foster a proactive approach among the team.
- Automate Risk Management - If you do not have team members or in-house cybersecurity specialists, a cost-effective option could be the use of automated tools like security monitoring systems, vulnerability scanners, and Governance, Risk, and Compliance (GRC) platforms to streamline risk management and documentation. These tools enable continuous monitoring, real-time alerts, and data-driven risk analysis, ensuring that emerging threats are detected and addressed before they can spiral out of control.
- Include all Departments - Involving cross-functional teams in your company’s risk management is essential, as risks often span multiple departments. Collaborative risk assessments, drawing from the expertise of IT, HR, legal, and operations teams, provide a comprehensive understanding of potential vulnerabilities and raise awareness around the importance of effective information security practices. By embedding risk management into everyday decision-making and processes, your organization can align its security posture with ISO 27001 standards and stay ahead of the myriad of evolving security risks.
How Does ISO 27001 Risk Management Work in the Real World?
In theory, performing ISO 27001 risk assessments may seem straightforward, but they can be hard to understand out of context.
Here are a few scenarios where effective Risk Management may be critically important:
Managing Cloud Security
Many companies in the tech industry migrate their services to the cloud, which can raise concerns about security and compliance, because they are effectively moving critical data and processes outside of their own infrastructure to a third-party provider. When data is stored in the cloud, organizations no longer have direct control over the infrastructure that houses their data. This can make it difficult to ensure that data is being handled securely, especially in a shared or multi-tenant cloud environment.
Cloud environments can often be targets for cyberattacks. Attackers may exploit misconfigurations, insecure APIs, or vulnerabilities in the cloud infrastructure to gain unauthorized access to sensitive data. In the cloud, security operates under a shared responsibility model. The cloud provider is responsible for securing the underlying infrastructure, but the organization is responsible for safeguarding its data, applications, and access management. Misunderstanding or neglecting these responsibilities can lead to gaps in security, such as misconfigured storage or insufficient identity and access management controls.
If your organization uses cloud computing, under ISO 27001 you are required to implement cloud security controls such as encryption, access control policies, and audit trails for all data stored in the cloud. This is another opportunity to use automated monitoring tools so that you can easily and continuously track access to your company’s cloud resources. Your organization should also undergo routine audits to ensure compliance with ISO 27001, and conduct risk assessments to identify new vulnerabilities as the cloud environment evolves.
Protecting Personal Information
Organizations that handle sensitive personal information or PII (Personally Identifiable Information), like those in the healthcare industry are required by HIPAA and other laws/regulations to implement certain safeguards to protect their patients’ data. Many of these organizations also implement ISO 27001 particularly if they have an international footprint or work with international providers.
Organizations that store patient records must implement specific controls, like encryption, for all patient records while in transit or at rest. They should also maintain secure backups to ensure that patient information is accessible even in the event of system failures, outages, or other incidents like ransomware attacks.
Healthcare companies must also conduct a Business Impact Analysis (BIA) to get the full picture of how their business and patient care could be affected by attacks or system disruptions. This enables companies to prioritize necessary functions for continued patient care. Because of the high level of risk to personal information and data, it is crucial to implement regular penetration tests and vulnerability scans on the organization’s systems.
Another control that healthcare companies should implement is role-based access control (RBAC), which prevents insider threats and the mishandling of sensitive information by limiting access to sensitive data based on job function. While RBAC is not explicitly named by ISO 27001 as a requirement, it falls under Annex A.9 - Access Control.
Safeguarding Financial Information
Like healthcare organizations, financial services companies are required to uphold legal regulations and compliance frameworks such as GLBA for financial institutions in the United States. While ISO 27001 is voluntary, it can help institutions meet many of the same objectives as GLBA but also covers broader security controls and offers protection from a wider range of threats. It also aligns with other global regulatory frameworks, helping financial institutions manage international operations.
To mitigate a diverse array of sophisticated cyber risks, under ISO 27001, a financial company might deploy an automated threat detection system (SIEM) that monitors network traffic and user behavior in real-time, detecting potential threats early. The institution must also introduce MFA for both employees and customers, adding an extra layer of security to prevent unauthorized access, even if credentials are compromised.
As part of their control implementation, they could also conduct regular risk assessments to identify vulnerabilities and implement other technical controls, such as firewalls, encryption, and network segmentation. These measures limit malware spread and ensure system integrity. Lastly, they could also require employees to undergo security awareness training, including phishing simulations, to reduce the likelihood of falling victim to attacks.
These real-world scenarios demonstrate how regardless of industry or sector, ISO 27001 can help organizations implement crucial controls within a strategic framework to prevent operational disruptions and cyber attacks and manage potential and existing risks effectively.
III. Conducting Internal Audits
An internal audit is just what it sounds like - an audit conducted by your employees or hired consultants to assess whether or not your company’s ISMS satisfies ISO 27001 requirements. The requirements for an ISO 27001 internal audit are explained in clause 9.2.
ISO 27001 requires that internal audits:
- Follow an audit program created by the organization itself.
- Are conducted at routine intervals. (ISO 27001 does not specify how often these internal audits should be conducted, but once per year is recommended).
- Determine whether or not the organization’s ISMS meets the ISO 27001 standard as well as the organization’s own standards.
- Are documented as a formal audit.
- Are performed by an impartial employee (or employees) not involved in the creation/implementation of the ISMS and with no operational control over the ISMS. The auditor can also be an external auditor hired by the company to perform the audit. Though the auditor is outside of the company, they can still count as an internal auditor.
- Create an audit report that is shared with organizational management and kept as a record of the audit.
You may also like: Security Audit Checklist
What is the Purpose of an Internal ISMS Audit?
An internal audit will provide your organization with an opportunity to evaluate the success of the ISMS within the context of your business objectives and operations. It also helps you catch issues and identify areas for improvement that you otherwise may not have spotted.
Other benefits of performing an internal ISMS audit include:
- Enabling you to identify non-conformities and vulnerabilities before a security incident occurs
- Identifying new security threats as they arise
- Offering an occasion to communicate changing security requirements or information security policies to employees and stakeholders
- Ensuring employees remain familiar with their roles and responsibilities as outlined by the ISMS
- Identifying areas where ISMS can be adapted and improved
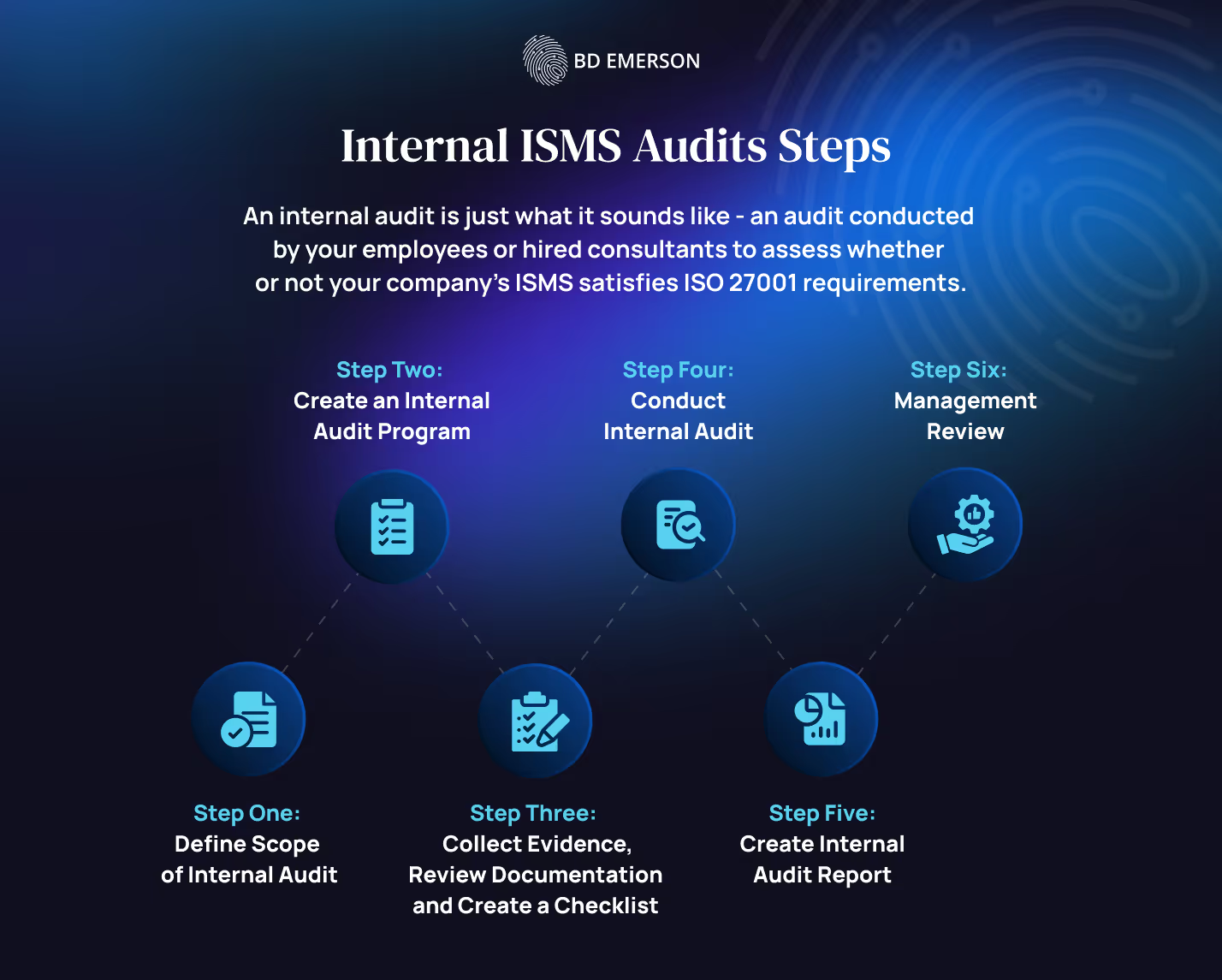
Step 1: Define Scope of Internal Audit
Precisely define the scope of the internal audit, zeroing in on specific processes, systems, departments, or controls within your ISMS. This could include evaluating the implementation of ISO 27001 controls (recommended ahead of undergoing an external ISO 27001 audit), assessing risk management processes, or reviewing the effectiveness of incident response mechanisms.
Then, establish the audit objectives based on the ISMS scope, determining the specific Annex A controls, risk treatment plans, and policies that need to be assessed. This helps ensure the audit targets areas critical to maintaining the ISMS's effectiveness and alignment with the organization’s security objectives and ISO 27001 compliance requirements.
Because of the large number of controls implemented during the ISO 27001 process, it is often a good idea to create an audit checklist of them and divide and conquer between auditors.
Step 2: Create an Internal Audit Program
Before embarking on an internal audit, your organization will need to develop an audit roadmap or program. The internal audit program is a structured plan that outlines the overall approach, resources, and activities necessary to carry out the ISMS audit. It should include the frequency at which your organization will conduct internal audits, the methodology to be used, and the roles and responsibilities of the individuals carrying out the audit. You will also need to implement reporting mechanisms and procedures for corrective actions following the audit.
Step 3: Collect Evidence, Review Documentation and Create a Checklist
As you prepare for the internal audit, gather relevant evidence and review ISMS documentation to assess the effectiveness of the security controls and management system of your organization. This may involve examining risk treatment plans, security policies, access control lists, incident reports, and vulnerability management logs. Some core documents you will need to review include:
- ISMS Scope Statement: specifies the boundaries to which ISMS applies
- ISMS Statement of Applicability: specifies the controls that have been selected and implemented and provides justification for the ones which aren’t applicable
- Information Security Policy: outlines the security goals of the organization and the SOPs in place to achieve them
- ISO 27001 Risk Assessment and Risk Treatment Plans: present the approach to identifying risks, the criteria for scoring them and the action plan for treatment
- Definition of Responsibilities: outlines the roles and responsibilities of individuals in control implementation
- Asset Inventory and Acceptable Use: consist of asset inventory and guidelines on fair use
During this review, you will want to make a checklist of both ISO 27001 requirements and the requirements of your organization’s security program so that you can reference the checklist as you perform the audit. Many templates exist online for an ISO 27001 internal audit checklist, but an easy way to arrange your checklist is to create four columns:
As you collect evidence and documentation, make sure that it reflects the current operational state of the ISMS. Pay attention to areas like information asset registers, security monitoring reports, and audit logs, ensuring that all critical data is captured for review.
Step 4: Conduct Internal Audit
Once you have defined the scope of the internal audit, selected auditors, compiled documentation and a checklist, and divided the checklist between auditors (if there are multiple), the audit can begin. Auditors will test ISMS controls, interview control owners, and verify operational practices, including the implementation and performance of security controls like data encryption, access control, and incident management.
Following a structured audit methodology and employing compliance tools will facilitate testing the ISMS’s controls against ISO 27001’s requirements and the organization’s risk profile. Auditors will need to identify non-conformities where they find that controls are ineffective or missing and evaluate whether risk management processes are appropriately mitigating identified risks. As part of the audit, it may be important to run technical tests, like a log analysis, vulnerability assessments, and security configuration reviews.
Auditors need to gather sufficient and appropriate evidence to support their findings. In addition to control testing and system logs, evidence can be collected through employee interviews and observation. All evidence will need to be validated as authentic and complete, ensuring that it accurately represents your organization’s security posture.
Step 5: Create Internal Audit Report
Once the auditors have finished actively investigating and observing your organization’s ISMS, they will craft a report of their findings, including the evidence they have gathered. They may also include the audit checklist you created along with any documentation of the audit program in order to produce a detailed report.
The report should
- Include the scope, objectives, and extent of the audit
- Detail the auditor’s findings on which policies, procedures, and security controls are effective and which are not, supported by evidence
- Identify and label non-conformities
- Include corrective actions, recommendations, and remediation plans
Once the report is finished, it is time to present it to management for further review and the eventual creation of an action plan.
Step 6: Management Review
Ideally, top management at your organization will have been included in the audit process from the beginning, as they are often the ones approving the audit program and appointing/hiring auditors. Once the audit report is completed, management or executives at your organization will need to review it so that they can effectively prioritize issues based on risk and impact, allocate resources for remediation, and establish timelines for implementing corrective measures. The management review is a vital way to ensure that the ISMS is in alignment with the company’s business objectives and compliance requirements.
Handling Non-Conformities During the Internal Audit
The internal audit doesn’t end with the management’s review of the audit report. A key purpose of the internal audit is to identify and address non-conformities found within your organization’s ISMS. When it comes to handling these non-conformities, your audit team will need to follow these steps:
- Identify Non-Conformities: The auditor compares actual practices against the organization's policies, procedures, and ISO 27001 requirements to detect gaps or non-compliance.
- Document Findings: Each non-conformity is clearly documented, including the specific control, policy, or procedure that was violated, along with supporting evidence (e.g., logs, interviews, observations).
- Classify Non-Conformities: Non-conformities are categorized based on severity (e.g., minor, major), with major issues posing significant risks to security and compliance.
- Immediate Corrective Action: If a critical non-conformity is found, the auditor may recommend immediate corrective actions to prevent further risk or damage.
- Root Cause Analysis: Investigate the underlying cause of the non-conformity to prevent recurrence, focusing on systemic issues rather than just fixing symptoms.
- Propose Corrective Actions: The auditor may suggest specific corrective actions for each non-conformity aimed at addressing the root cause and restoring compliance.
- Create a Corrective Action Plan (CAP): Your organization, in collaboration with management, must create a CAP that assigns responsibility, sets deadlines, and outlines steps to resolve each non-conformity.
- Follow-up and Verification: A follow-up audit or review should be conducted to verify that corrective actions have been implemented and the non-conformities have been resolved effectively.
Best Practices for Internal Auditing
Leveraging Third-Party Tools and Automated Auditing
Using third-party tools like Vanta for continuous monitoring helps your company remain compliant. Vanta’s sophisticated platform flags vulnerabilities and provides remediation steps, helping to proactively manage security risks. Automated tools like Vanta are especially useful in guiding your company through a risk assessment and gap analysis that align with ISO 27001 requirements.
Using third-party tools that are equipped to track and store control documentation assists your team in organizing and compiling the necessary evidence of your security controls and infrastructure that are crucial to succeeding an audit. Additionally, as you continuously evaluate your alignment with ISO 27001 standards, tools like Vanta will track the effectiveness of implemented controls over time, making sure that they are continuing to function appropriately.
Training Internal Auditors
It is possible to hire external auditors to perform your internal ISO 27001 audits. Though they are technically external to the organization, they are still performing the audit on behalf of the company and can be considered internal for this reason.
If you choose to train existing employees to perform an audit, however, you should incorporate the following best practices into their preparation:
- Formal Training on ISO 27001: Make certain auditors understand the structure, control objectives, and Annex A controls of ISO 27001.
- Auditing Principles Training: Cover auditing methodologies, including planning, execution, reporting, and identifying non-conformities.
- Hands-on Workshops and Simulations: Provide practical training through real-world scenarios so employees can practice audit skills in a controlled environment.
- Communication Skills Development: Train auditors to effectively conduct interviews, interact with departments, and communicate findings clearly.
- Documentation Review: Develop skills to assess and verify documentation and evidence for compliance with ISO 27001 requirements.
- Continual Learning: Provide ongoing training to keep auditors updated on changes to the ISO 27001 standard and emerging security risks and technologies.
- Foster Independence and Objectivity: Encourage unbiased evaluations by maintaining auditor independence and objectivity throughout the audit process.
It is essential to properly equip internal auditors with the skills and knowledge they need to assess the effectiveness of your company’s ISMS. Incorporating these best practices into auditor training will preserve the integrity of the internal audit and set your organization up for success.
Conducting Post-Audit Reviews
Once the internal audit results have been received, the real work begins. Companies should assemble important stakeholders, including the audit team, department heads, and management, in order to discuss the results of the audit. The main goal of the review is to examine both the non-conformities identified and areas of improvement, verifying that there is a clear understanding of the issues and their potential impact on the organization’s Information ISMS.
Best practices include prioritizing findings based on risk severity, setting realistic deadlines for corrective actions, and assigning responsibility for implementing these actions. Additionally, it's important to ensure transparent communication during the review process, allowing stakeholders to ask questions and offer feedback. Follow-up audits or regular status updates should be scheduled to monitor the progress of corrective actions.
TIP: Documenting lessons learned from the audit, both positive and negative, can make future audit processes run more smoothly.
IV. Management Reviews
According to Clause 9.3, an ISO 27001 compliant organization must perform planned Management Reviews at least once per year and within an external audit surveillance period.
What is the Purpose of a Management Review?
The Management Review provides an opportunity for senior leadership to evaluate the effectiveness of the ISMS, assess whether it is aligned with your organization’s strategic objectives, and verifies that adequate resources are in place to support information security initiatives. One of the key elements of a successful ISMS is the support and commitment of senior management and company executives. By conducting routine reviews of the ISMS and its implementation, your management team prioritizes continual improvement and compliance.
When the organization is in the early stages of implementing its ISMS, management should be highly involved and even participate in weekly reviews where they can continue learning about ISMS implementation while also working with their teams to set goals for the ISMS and future audits.
What to Include in Your Management Review
Following a thorough audit, management team members should narrow their efforts to focus on the following:
Performance Metrics
By evaluating security incidents, audit results, non-conformities, and corrective actions that have been identified, management will get a succinct picture of the performance of the ISMS and where it can be improved.
New Information
Noting changes in external and internal issues that may affect the information management security system is key to maintaining relevant controls and keeping pertinent issues top of mind.
Evaluation of Risk Management Process
The review should also include a look at the risk management process used by the company. How are risks being mitigated? Have any new risks emerged? What is the status of the risk treatment plan?
Proof of Legal/regulatory Compliance
Double-check that no laws/regulations have changed since the implementation of the ISMS, but if they have, be prepared to implement the approved standards.
Feedback on the information security performance
It is critical to look at the whole picture when evaluating an ISMS. Valuable insight can be gained from looping in stakeholders and seeking their feedback regarding the performance of controls. How do the controls and practices put into place align with work and business objectives across departments?
Resource Allocation
Management Reviews are essential for identifying areas that may need continual improvement and thus require more resources in order to thrive. For example, if a particular control is underperforming, management may decide to allocate additional resources or invest in new technologies to bolster that area.
Who Needs to Participate?
It is much simpler to get management on board during a review when you have included them from the beginning and they understand the scope and resources required of an effective ISMS. Not only is the process simpler when management is included, it also fulfills a requirement of Clause 5.1, which pertains to leadership and commitment.
To create a more focused approach, forming an ISMS-specific board or team of executives is recommended. Typically an ISMS board includes the Chief Information Security Officer (CISO), members of senior management, and the individuals managing the ISMS in practice. These ISMS board members can also hold information security roles as outlined in the ISMS - the roles need not be exclusive, but clear expectations for each role should be documented.
Creating Actionable Insights
Taking the findings from the review into consideration, the management team can begin to identify action steps for improving the ISMS and addressing any gaps. After discussing the review outcomes, management should focus on setting specific objectives that address the identified issues. For instance, if the review reveals frequent security incidents due to weak access controls, a clear objective could be to enhance user authentication protocols within a set timeframe. To achieve this, management may decide to allocate additional budget for new access control software or implement a multi-factor authentication system to reduce unauthorized access incidents.
Identifying areas that require improvement often involves prioritizing the most pressing risks based on their severity and potential impact on the organization. If audit results indicate that data encryption controls are insufficient, which could put sensitive customer information at risk, this issue should be prioritized over lower-risk concerns. A detailed plan would then be developed, including specific actions such as upgrading encryption standards, ensuring all data-at-rest and data-in-transit are secured, and training staff on the new procedures. This kind of strategic prioritization ensures that the most significant risks are addressed first, aligning with ISO 27001’s emphasis on a risk-based approach to security.
Review Frequency
Management reviews must take place at least once per year and within an external audit surveillance period. Organizations should consider more frequent management reviews due to the ever-changing threat landscape and the large volume of information that must be reviewed to ensure that the ISMS is operating successfully in the face of sophisticated risks.
In the early phases of the Stage 1 audit, more frequent reviews on a weekly or monthly basis, will help your organization’s leadership collect evidence and build the habit of evaluating the ISMS and its controls. It is equally important to establish an agenda for each review so that your ISMS board is tackling the issues that are highest in priority.
Documenting Review Outcomes
As with all steps of the ISO 27001 implementation process, it is essential to document the participants, frequency, findings, and action steps identified during the management review. Among your documentation, you should include a summary of the discussions, any decisions made, and clear directives on next steps.
Specific individuals or teams should be assigned responsibility for implementing each action, and deadlines should be put in place. Documenting the review’s outcomes provides a formal record for future audits and assessments and also reinforces accountability across your organization.
V. Filling in your Statement of Applicability (SOA)
The Statement of Applicability is a fundamental part of your ISMS, and one of the most important documents you will create for your ISO 27001 certification. This document will explain which of the 93 Annex A security controls are or aren’t applicable to your organization’s ISMS. Its primary purpose is to justify the inclusion or exclusion of each control, showing a clear rationale behind the chosen security measures and ensuring they align with identified risks, legal requirements, and business objectives. The SoA provides transparency for internal and external audits, demonstrating how your organization tailors its ISMS to address specific security needs, manage risks, and meet compliance obligations. It acts as a roadmap for implementing and maintaining effective security controls.
NOTE: The Statement of Applicability is internal, confidential, and only meant to be shared with the ISO 27001 auditor.
Selecting the Security Controls that Apply to Your Organization
Once you have completed a risk assessment and established a risk treatment plan, you can begin to review the 93 security controls outlined in Annex A. After you’ve identified the risks that you need to address through the use of security controls, you can get started.
The 2013 iteration of ISO 27001 contained 114 controls that were divided into 14 categories. The most updated version of the standard, from 2022, outlines 93 security controls divided between four themes:
- Organizational
- People
- Physical
- Technological

Organizational (37 controls)
Organizational controls hone in on the procedures, processes, policies, responsibilities, and other operational measures required for effective information security. This theme prioritizes governance and risk management strategies that support an organization’s business objectives.
These controls include:
- Policies for information security
- Information security roles and responsibilities
- Segregation of duties
- Management responsibilities
- Contact with authorities
- Threat intelligence and monitoring
- Classifying and labeling information
- Identity and access control
- Asset management
These are not all of the organizational controls, but they demonstrate the focus areas of the organizational theme.
People (8 controls)
This theme centers on managing the human factors that affect information security and includes:
- Pre-employment screening
- Terms and conditions of employment
- Information security awareness, education, and training
- Disciplinary process
- Responsibilities after employment
- Remote work
- Reporting security events
The people theme focuses on preventing and responding to the consequences of human behaviors like negligence, errors, or intentional breaches. Some controls in this category manage the lifecycle of employment so that employees and contractors are onboarded and offboarded as securely as possible.
Physical (14 controls)
The third theme focuses on the physical environment of the ISMS and emphasizes access control, threat mitigation, and asset lifecycle security.
Controls in this category are related to:
- Physical security perimeter
- Physical entry controls
- Securing offices, rooms, and facilities
- Protecting against physical threats
- Secure disposal or reuse of equipment
- Clear desk and clear screen policy
Technological (34 controls)
The technological theme encompasses controls that address the security of technology assets, systems, and data. These controls aim to ensure secure use, access, and management of technology throughout its lifecycle.
Some technological controls include:
- Employing privileged access
- Network security tools
- Secure information transfer
- Secure configuration of information security systems
- Cryptographic controls
- Logging and monitoring
- Information Backup
- Secure Development and Testing
These controls are critical in protecting an organization’s information security infrastructure from evolving cyber threats. By securing systems, applications, networks, and data, these measures minimize risks, ensure business continuity, and maintain compliance with regulatory requirements.
How to Choose Relevant Controls
Because the standard is designed to be risk-based and tailored to an organization’s unique context, including its business requirements, operational environment, and risk profile, not all controls in Annex A will be relevant to your organization. This means you will need to determine which controls your organization will need to implement.
Here are a a few things to consider as you determine the necessary controls for your organization:
1) Review Risk Assessment Results to Identify Problem Areas
As mentioned above, a comprehensive risk assessment is crucial in order to Identify assets, threats, and vulnerabilities, and evaluate potential impacts and likelihood. This prioritized risk list helps pinpoint areas needing controls, ensuring that the selected measures specifically address organizational risk. Comprehensive risk assessment forms the foundation for deciding relevant and effective controls in the SoA.
2) Consider Legal, Regulatory, and Contractual Obligations
Review applicable laws, regulations, and contracts to identify required controls. For example, data protection regulations may necessitate encryption and data access measures. By meeting these external obligations, your SoA ensures legal compliance and addresses contractual security commitments.
3) Evaluate Business Objectives and Strategic Goals
Align controls with broader business and strategic goals, ensuring security measures support critical objectives like data availability or continuity. Controls should enhance your business’s operational resilience, aligning with essential organizational priorities while ensuring the ISMS supports long-term strategic initiatives.
4) Prioritize Based on Risks or Resources
Focus on high-priority controls that mitigate significant risks, factoring in available resources and potential investment required. Implement essential controls first, adjusting as your organization’s resources allow. This risk-based prioritization ensures the most impactful controls are established promptly within existing constraints.
5) Document Justifications for Each Control
For each control in the SoA, document its purpose, detailing the risks it addresses or regulatory needs it meets. Also, justify any exclusions to ensure transparency. Thorough documentation supports internal understanding and audit clarity, highlighting the rationale behind the control selection.
6) Review and Update as Needed
Regularly reassess controls to adapt to changes in risks, regulations, and business requirements. A dynamic SoA ensures the ISMS remains relevant, effective, and compliant with changing security landscapes. Scheduled reviews allow for proactive adjustments, maintaining an adaptive security approach.
Mapping Risks to Controls in the Statement of Applicability
A simple way to track the controls listed in the SoA is by creating a spreadsheet with a row for each control in Annex A.
Example:
Using a similar structure to organize the control requirements in your SoA will facilitate the risk mapping process and provide a key piece of documentation that your team can use not only as a fulfilled requirement of ISO 27001 certification, but as a clear roadmap. This is where the applicability piece starts to solidify. You compare your risk against all relevant Annex A controls, and you justify why these controls are required or not required, therefore outlining which controls apply to your organization’s ISMS.
This structure ensures that the controls selected are in fact driving value towards the risk reduction, by requiring your organization to review and produce the Statement of Applicability. If it is simpler to start by identifying risks and then finding all applicable controls, instead of starting with controls and finding applicable risks, that works too.
Example:
Malware Infection Compromising Systems
CONTROLS
- Malware Protection (A.12.2.1): Install and maintain anti-malware software on all endpoints to detect and quarantine malicious software.
- Secure Configuration (A.14.2.1): Follow secure configuration guidelines for servers, workstations, and networks to reduce malware exposure.
- Restricting Software Installation (A.9.4.3): Limit installation rights to authorized personnel, reducing the risk of malware being installed accidentally.
As you map out the controls that apply to the risks you’ve identified, remember to stay within the scope of your ISMS. While it is important to avoid having more than a handful of exclusions, it is also essential to only identify risks that are relevant to the scope of the ISMS in your SoA.
Documenting Exclusions
What should you do with controls that don’t fall within the scope of your ISMS? Perhaps the control does not apply to your organization’s operations or risk environment; no matter the reason, make sure to document the specific controls that you are excluding from your ISMS in the SoA.
Though you should have minimal exclusions, it is crucial to provide a clear justification for the exclusions you do identify in your SoA.
Here are a few examples of justifications you can include in your SoA:
Non-Relevance
Clearly explain why the specific control does not apply to your organization’s context. This could be due to the nature of your business operations, services, or products. For example, if your company doesn’t process or store customer credit card data, you could justify excluding controls related to payment card industry standards.
Acceptable Level of Risk
Reference your organization's risk assessment to justify exclusions. If a control addresses a risk that is not relevant to your business, document this. For example, if a control mitigates a risk that your risk assessment has identified as very low or nonexistent, this can serve as justification for exclusion.
Alternative Controls
If you’ve chosen not to implement a specific control because you have alternative mechanisms in place that achieve the same level of security or compliance, you should describe these alternatives in detail. For instance, if a control prescribes the use of physical security measures, but your organization is fully cloud-based, you may explain how virtual security measures address the same concerns.
Regulatory or Contractual Scope
Justify exclusions based on the regulatory or contractual scope of your ISMS. If certain regulatory requirements or contractual obligations do not apply to your business, this can be a valid reason for exclusion. Document these exclusions by referencing the relevant legal or contractual boundaries.
Operational Limitations
Sometimes, specific operational or technical limitations prevent the implementation of a particular control. Justify the exclusion by explaining these constraints, such as a lack of applicable infrastructure or tools.
Industry Standards
If the control is geared toward industries or operational models that do not align with your own (e.g., manufacturing controls for a software company), justify the exclusion by referencing how industry standards differ for your type of business.
TIP: When justifying exclusions in your SoA, be transparent, thorough, and make sure that exclusions are based on a logical assessment of your organization’s operations and risks.
How Often You Need to Update Your SoA
Like with your ISMS, your SoA should be reviewed at least annually and updated with any new developments as part of your annual internal audit or management review. This ensures that any changes in business processes, risks, or the regulatory landscape are reflected in the current controls.
Other occasions when you should consider updating your SoA include:
- After significant changes: Examples of significant changes may include: Changes in business operations, structure, or processes; the introduction of new technologies or systems; changes in regulatory or contractual obligations; changes in the organization’s ISMS such as new or modified security controls. These changes may require the addition, removal, or modification of controls in the SoA.
- After internal or external audits: Update the SoA following internal or external audits if new findings suggest adjustments to controls. If the audits identify any gaps in your security controls or if corrective actions are recommended, the SoA should reflect those changes.
- In response to security incidents: If a security incident occurs, the SoA should be revisited to confirm that relevant controls are effective. This may lead to updates in the SoA to address new risks or weaknesses uncovered during the incident response.
- When risk assessments are updated: Anytime the risk assessment process identifies new or changing risks, the SoA should be updated accordingly. ISO 27001 requires that risk assessments be conducted regularly, and the SoA should align with the latest risk landscape.
- During recertification: ISO 27001 certification is typically valid for three years, with a surveillance audit conducted annually. At the time of recertification, a thorough review and update of the SoA is required to ensure it accurately reflects the current scope of the ISMS and that all controls are still valid.
As your organization’s ISMS evolves, it is critical that your SoA evolves as well to incorporate and reflect any control changes to your ISMS.
VI. Implementing Core ITGCs in a Cost-Effective Way
Information Technology General Controls (ITGCs) are controls that ensure the secure and effective operation of IT systems, processes, and infrastructure within an organization. They are designed to protect your organization’s data from unauthorized use, disclosure, or compromise.
ITCGs are essential for ISO 27001 because they provide the foundational framework that supports the overall effectiveness of your company’s ISMS. ITGCs provide support for information security controls, preserve the integrity of your organization’s data and systems, mitigate risks, verify that IT systems function as intended, and fulfill compliance requirements for multiple frameworks.
ITGC Categories
ITGCs typically cover the following areas:
Access Controls
These controls manage who has access to the organization’s systems and data, ensuring that only authorized users can access sensitive information. This includes user authentication (e.g., passwords, biometrics), role-based access control, and user provisioning/de-provisioning.
Change Management
Controls that govern how changes to IT systems (such as software updates, configuration changes, or patches) are managed. Change management ensures that all modifications are reviewed, tested, and authorized before being implemented, reducing the risk of introducing vulnerabilities or disruptions.
Backup and Recovery
Controls that ensure critical data and systems are regularly backed up and can be recovered in case of an incident or disaster. This is crucial for business continuity and protecting data from loss due to hardware failure, information security attacks, or other incidents. Some controls in this category include setting up automated backups, offsite storage of backups (either physical or cloud-based), and regular backup testing.
IT Operations
These controls cover the management of your organization’s day-to-day IT operations, such as monitoring system performance, incident management, and verifying that systems are running efficiently. IT operations also include preventive measures to avoid downtime and regular maintenance activities.
Physical and Environmental Security
ITGCs also extend to the physical security of IT assets, including access to data centers, servers, and hardware. Environmental controls, such as fire detection, power supply, and cooling systems, help protect your company’s physical infrastructure from damage or disruption.
System Development and Maintenance
These are controls related to the secure design, development, and maintenance of software systems. This includes verifying that development processes follow security best practices, that systems are tested before deployment, and that vulnerabilities are addressed throughout the software lifecycle.
Permanent ITGCs vs. Triggered ITGCs
There are also permanent ITGCs and those that are triggered by events.
Permanent ITGCs: Ongoing, always-active controls that continuously monitor and protect your organization’s IT environment. They do not depend on specific events or conditions to be activated. Permanent controls are supposed to maintain a stable and secure environment by providing constant oversight over critical areas like access control, change management, data backup, and system monitoring.
Examples of permanent ITGCs are:
- Access Controls: Permanent restrictions on user access to sensitive systems or data.
- Change Management: Procedures that always govern how updates or changes to systems are requested, approved, and implemented.
- Backup Procedures: Regular, automatic backups of critical data at scheduled intervals.
- Monitoring: Continuous log reviews and system performance tracking for potential anomalies.
These types of permanent ITGCs make certain that only authorized personnel can access sensitive customer data at all times, not just in response to a specific incident.
Triggered ITGCs: These controls are activated by specific events or conditions. They are reactive in nature and are deployed when certain criteria or thresholds are met. Triggered controls respond to particular risks or changes in the environment, ensuring that special actions are taken when flagged scenarios arise.
Examples of triggered ITGCs are:
- Incident Response: Controls that activate when a security breach or other incident is detected, such as locking down affected systems.
- Disaster Recovery Procedures: Initiated in response to system failures or data loss events.
- Audit Log Reviews: Triggered when suspicious activity is detected based on predefined thresholds, like multiple failed login attempts.
- Temporary Access Controls: When elevated access is needed for a short period during an emergency situation, and is automatically revoked after the event.
When a security breach is detected, triggered controls may lock out unauthorized users, alert IT teams, and initiate backup recovery processes.
Key Differences
Permanency vs. Conditional Activation:
Permanent controls operate continuously, regardless of external events or conditions. They form the backbone of an organization's IT security and governance framework and are built into the fabric of your IT system, running in the background 24/7. Permanent controls establish a baseline level of security and are essential for ensuring that standard operations are consistently performed within the approved guidelines.
Triggered controls are condition-based, activating when predefined conditions are met, or specific events occur. They are not in place at all times but are triggered by system events, anomalies, or environmental changes and are designed to protect your organization from situations that fall outside of normal parameters.
Proactive vs. Reactive:
Permanent controls like continuous network monitoring that alerts security teams when anomalies in traffic patterns are detected (e.g., unusual data transfer volumes) are proactive. They are always running and scanning for potential issues. These controls are in place to proactively secure data, systems, and processes on an ongoing basis, so that your organization operates within secure parameters from the outset.
Triggered controls like automatic backups are triggered when specific thresholds, such as high disk usage or certain error messages, are met. Their role is to contain and mitigate the impact of these events, like incident response systems or disaster recovery plans.
NOTE: Proactive, permanent controls are preventative, while reactive, triggered controls are used to handle exceptions or emergencies.
ITGCs: Scalability and Future-Proofing
As you build ITGCs into your organization’s processes, follow a systematic approach that takes into account the current IT environment and how it may evolve along with your company’s goals and objectives.
Here are a few examples of how you can build ITGCs that are scalable and future-proof:
1) Automate Where Possible
Again, utilizing automated control management programs for access management, change management, and monitoring systems will be your best bet for minimizing human error and enabling consistent control enforcement.
Some automation tools we recommend are:
- Vanta - Compliance / Security Automation
- Unbound Security - Securing authorized AI usage
- Autharva - Automated Identity and Access Management
2) Employ Risk-Based Controls
Focus on risk-based ITGCs, and prioritize controls that address the most critical risks to your business. This allows controls to scale efficiently, as they concentrate resources on high-impact areas while remaining adaptable to emerging threats. An example of this would be applying heightened controls for high-risk data and systems while maintaining lighter governance for lower-risk areas and adjusting as your risk profile evolves.
3) Adopt Modular and Configurable Control Frameworks
Fortunately, ISO 27001 is a modular control framework, offering a flexible approach to implementing controls across your business in a way that aligns with your company’s goals. ISO 27001 allows you to configure ITGCs based on the results of your risk assessment, not in a one-size-fits-all approach. With a modular framework, it becomes much simpler to scale and evolve your ITGCs over time, staying up to date with new requirements and emerging threats.
4) Use Cloud-Native Solutions
Cloud-native ITGC solutions can inherently scale to handle growing infrastructure and workloads. They provide the flexibility to quickly adopt new technologies and services while ensuring your company’s security controls remain effective. Cloud-based security and monitoring tools can automatically scale, which can be especially useful if your organization faces increased data traffic, new users, or new applications.
5) Conduct Frequent Control Reviews
As with your ISMS at large, it is crucial to perform periodic reviews of the ITGCs that your organization implements, so that they remain relevant and effective. You will likely review your ITGCs on an annual basis as you review your ISMS and Statement of Applicability. Make sure to also conduct control reviews whenever your organization faces significant changes or incidents. It’s also important to establish a process for performing these reviews so that they progress smoothly and your team does not have to “reinvent the wheel” each time.
6) Collaborate across Teams
Collaborate with different departments, such as compliance, IT, and operations, to ensure that ITGCs are integrated across the organization and can support future growth. This alignment makes controls more scalable across various business units and keeps teams on the same page when it comes to expectations surrounding controls. Additionally, working with compliance teams to ensure ITGCs are aligned with ISO 27001 and your ISMS is critical, especially when it comes to incorporating feedback from various teams to enhance scalability.
7) Leverage AI Tools
AI and machine learning can enhance scalability and future-proofing by enabling more sophisticated monitoring, predictive analytics, and real-time threat detection. These technologies help ITGCs adapt to new types of risks and vulnerabilities. Using AI tools can save your team time so that they can continue performing the critical daily operations of your business, knowing that your organization’s systems are covered.
8) Scale through Cloud or Hybrid IT Infrastructures
Another way to ensure your ITGCs will scale is by leveraging hybrid cloud architectures that allow ITGCs to span across on-premises and cloud environments. Therefore, as the business scales or adopts new cloud-based solutions, ITGCs can easily be applied to the expanded infrastructure. For example, implementing hybrid IT governance platforms that can monitor both on-premise and cloud resources will allow for the consistent application of security controls across different environments.
Cost-Effective Implementation Strategies
Implementing ITGCs can be costly if you don’t leverage the resources at your disposal effectively. Here are a few ways you can maximize cost-savings as you work to integrate ITGCs into your organization’s processes.
1) Leverage Existing Tools and Resources
Maximize your current IT infrastructure: Before investing in new tools, audit your existing systems and processes to identify whether they already have functionalities that support ITGCs. Many IT systems have built-in security features like access controls, audit logs, and change management modules.
Use open-source or low-cost tools: Where applicable, consider open-source solutions or affordable cloud services that offer necessary security features (e.g., backup and recovery, access control, change management) without the high cost of enterprise solutions. For example, tools like Git for version control or AWS IAM (Identity and Access Management) for access control can provide essential ITGC functions at a lower cost.
2) Prioritize Risk-Based ITGC Implementation
Let the results of your risk assessment be your guide: Focus your resources on areas with the highest risk. A risk-based approach helps you allocate resources efficiently by implementing controls that have the greatest impact on protecting critical assets and mitigating the most significant threats.
Identify "must-have" controls: Not all ITGCs will be equally relevant to your business. Prioritize the implementation of key controls that are aligned with your specific risk profile, such as access management, change control, and data backups, and leave less critical controls for future phases.
3) Automate Where Possible
Because of the vast amount of processes that need to be monitored, automation is often a time-saving and cost-effective solution, reducing the need for manual intervention. Examples of automating ITGCs include:
Automated access control management: Tools like Autharva can streamline user provisioning and de-provisioning, reducing the cost of manual oversight.
Automated backups and disaster recovery: Using cloud-based services like Google Cloud or AWS that offer automated data backups and easy-to-use disaster recovery solutions have become essential for companies that store data digitally and have accessible, cost-saving solutions for businesses of all sizes.
Automate evidence collection for audits: Tools like Vanta streamline compliance workflows by automating evidence collection, reducing the manual effort required of managing audit preparation. This saves employees time and enables them to focus on their core responsibilities.
4) Use Managed Services
Outsource non-core ITGC functions: Managed service providers can handle specific ITGC tasks such as network monitoring, system backups, or even patch management at a fraction of the cost of building in-house teams for these functions. BD Emerson offers robust IT-managed security services that include vigilant network infrastructure monitoring, robust end-user support, and proactive system management services.
Leverage cloud service providers: Cloud providers such as AWS, Azure, or Google Cloud offer many built-in security and compliance features like logging, access controls, encryption, and automated backup as part of their services. Oftentimes, this can reduce the costs of deploying and maintaining your own infrastructure.
5) Implement Gradually
Once you have implemented the controls necessary for ISO 27001 compliance, you can gradually implement controls beyond the scope of your ISMS if you are seeking certification with other frameworks.
Phased implementation: Start by implementing core ITGCs that are most critical to your operations, then gradually expand. By spreading the investment over time, you can manage costs and avoid large, upfront capital expenses.
Adopt a minimum viable product (MVP) approach: Implement the most essential aspects of each control first, focusing on basic functionality. For example, start with simple user access controls and progressively refine them with more sophisticated role-based access or multi-factor authentication as resources allow and your business grows.
6) Collaborate with Auditors Early
Don’t wait until right before the audit to connect with an auditor. Engaging with external auditors early during the implementation process can prevent expensive rework and adjustments later on. Auditors can provide guidance on where to focus your efforts and how to meet compliance requirements in a cost-effective way.
VII. Building Out ISMS Policies and Governance Policies
Security policies might invoke a groan – no one enjoys paperwork. Unfortunately, when pursuing ISO 27001, you can’t escape the requirement of creating policies that explain exactly what your business does to protect data. The policies required by ISO 27001 demonstrate to your employees, clients, vendors, partners, and auditors that you have documented every step taken to align your organization’s operations with the highest standard of information security.
Solid security policies are the foundation of a functioning ISMS, providing clarity and efficiency to your business operations. Some policies define the roles and responsibilities of your team members in managing your ISMS and maintaining compliance, which is essential in preventing important action steps from slipping through the cracks. As policies are the most requested documents when creating new partnerships or signing client deals, it’s critical that your policies are accurate and transparent.
Required Base Policies

Here is an overview of some of the policies required by ISO 27001 guidelines:
Information Security Policy
The Information Security Policy is a high-level policy that outlines the organization’s commitment to information security.
ISO 27001 Clause 5 states that an organization must have a set of information security policies that do the following:
- Outline your organization’s information security objectives and explain the purpose of the ISMS
- List any applicable legal, regulatory, or contractual requirements
- Assign roles and responsibilities by identifying those responsible for implementing, maintaining, and monitoring the ISMS’s performance
- Identify who the policy needs to be shared with internally or with external parties like vendors and contractors
- Define any resources or supplemental policies that will support your organization’s information security system
Data Protection Policy
This policy outlines how your organization collects, processes, stores, and protects personal data. It is designed to ensure that the organization complies with relevant data protection regulations, such as GDPR, the California Consumer Privacy Act (CCPA), and other privacy laws, while safeguarding the personal information of employees, customers, partners, and other stakeholders.
Data Retention and Disposal Policy
This document outlines how long your organization will retain different types of data and the procedures for securely archiving or disposing of data once it is no longer needed. The purpose of this policy is to ensure that data is stored for appropriate periods, complying with legal, regulatory, and business requirements, while also reducing the risk of holding onto unnecessary or outdated information.
Access Control Policy
The Access Control Policy defines how access to your organization’s systems, data, and physical resources is managed so that only authorized users can access sensitive information. It enforces security principles like least privilege, sets out authentication requirements, defines user access levels, and ensures compliance with legal and regulatory standards. The policy also outlines monitoring, auditing, and enforcement mechanisms to detect and respond to unauthorized access attempts.
Information Security Incident Management Procedure Policy
This policy provides a structured approach to detecting, responding to, and recovering from information security incidents. It includes steps for incident reporting, classification, response, and post-incident analysis. The procedure helps your organization minimize the impact of incidents, comply with regulatory requirements, and continually improve your incident response capabilities.
Asset Management Policy
This policy explains how your organization manages its physical and digital assets to ensure they are properly accounted for, protected, and used efficiently. The policy covers the identification, classification, security, and lifecycle management of assets, ensuring legal compliance. By maintaining a comprehensive asset inventory and assigning responsibility for asset management, the policy helps safeguard sensitive information, optimize resource use, and reduce operational risks.
Risk Management Policy
The Risk Management Policy outlines how your organization identifies, assesses, and manages risks that could impact its operations, assets, or compliance. The policy includes processes for risk identification, assessment, treatment (mitigation, transfer, acceptance, or avoidance), and monitoring. It defines roles and responsibilities, ensures compliance with legal and regulatory requirements, and emphasizes ongoing monitoring and incident management.
Information Classification and Handling Policy
This document explains how your organization classifies and manages its data based on sensitivity, value, and criticality. It ensures that all information is appropriately protected and handled according to its classification level, which helps prevent unauthorized access, loss, or misuse of sensitive data.
Information Security Awareness and Training Policy
The Information Security Awareness and Training Policy details your organization’s approach to verifying that all employees, contractors, and third-party users are educated and aware of the importance of information security. This policy provides guidelines for delivering training programs, ensuring that personnel understand their responsibilities in protecting the organization’s information assets and complying with ISO 27001 and other standards.
Acceptable Use Policy (AUP)
This policy is mostly self-explanatory. It outlines the acceptable and unacceptable use of your organization’s information systems, networks, and digital resources. It sets clear guidelines for employees, contractors, and third parties to follow when accessing company assets, ensuring responsible use, data protection, and compliance.
Other policies that may be required depending on the scope of your organization’s ISMS include:
- Mobile Device, BYOD, and Remote Work Policies
- Document Control Process and Controls for Managing Records
- Procedures for Working in Secure Areas
- Clear Desk and Clear Screen Policies
- Change Management Policy
- Data Backup Policy
- Data Transfer Policy
- Secure Software Development/Engineering Principles
- Supplier Security Policy
- Business Continuity Procedures
- Statutory, Regulatory, and Contractual Requirements
As we’ve already discussed security controls, it may be easier to think of policies as setting the overarching objectives and rules for how certain aspects of security will be managed by your organization. Controls, on the other hand, are the specific actions, mechanisms, and processes implemented to fulfill the objectives laid out in the policies. As you work through the creation of your policies, you will need to keep in mind the controls that you will have to implement to achieve the goals outlined by your policies.
Sync ISO 27001 Policies with Business Goals
To effectively customize ISO 27001 policies to support business operations, your team should develop policies that protect information security while accommodating the unique needs of your business’s daily workflows and strategic priorities. When policies are overly rigid or restrictive, they can block productivity and innovation, which can, in turn, undermine both security and progress. Customizing your ISO 27001 policies will enable your business to embed security into your operations without disrupting core operations.
Here are examples of how you can tailor ISO 27001 policies to fit your organization’s specific needs:
Establish Operational Priorities
Begin by analyzing core business functions and identifying the security requirements specific to each area. Collaborate with your department heads and key stakeholders to understand their unique operational needs and the challenges they encounter. For example, if remote work is integral to business operations, it’s essential to understand where employees are working, the tools they’re using, and the types of data they access remotely. This insight helps customize policies to ensure security measures protect remote access without compromising productivity.
Create Flexible Access Control Policies
Continuing with the example of remote work requirements - your Access Control Policy will need to be adaptable to support varied work environments. Instead of implementing restrictive access controls that could hinder efficiency, consider using role-based or attribute-based access control methods that grant access according to job roles, locations, or the devices your employees use. A flexible approach to access control will allow you to bolster the security of your systems and data without compromising productivity. For example, your remote workers could have limited access to high-risk systems unless specific conditions are met, such as connecting through a secure VPN or using multi-factor authentication.
Adapt Asset Management Policies for Diverse Environments
Since the start of COVID-19, many companies have migrated to a mobile and hybrid work environment model, which means employees often use a range of device types and ownership models (e.g., company-owned, personal devices, or BYOD) to work. Tailoring your Asset Management Policy to your organization’s specific needs will ensure that all assets, whether managed remotely or on-site, are secure. Some examples include requiring encryption and endpoint protection software on personal devices without limiting your employees’ ability to use these devices for work. You can also implement mobile device management (MDM) solutions to enforce security controls on personal devices used for work, achieving a balance between security and convenience.
Design Data Classification and Handling Policies to Support Operational Flow
An effective Data Classification and Handling Policy will focus on protecting your organization’s sensitive data but allow flexibility for non-sensitive data to flow freely to support business needs. By automating data classification where possible, your data will be labeled appropriately based on its sensitivity level. This way, non-sensitive information can be shared without cumbersome controls, while sensitive data is automatically flagged.
These are just a few illustrations of how you can customize your ISO 27001 policies in order to both fulfill ISO requirements and support the crucial functions of your business. ISO 27001 is more than a list of requirements - it offers a strategy for how to leverage security effectively to improve workflows. By creating flexible, clear, and relevant policies, your company can balance robust security with operational efficiency, enabling secure growth and agility across all areas of the business.
Establish Policies that Support Governance
Though the ISO 27001 standard is anchored in the confidentiality, integrity, and availability of information, it does not explicitly set out ethical or legal guidelines. Legal requirements and ethical principles do, however, align closely with the framework’s underlying goals and objectives regarding the handling of sensitive information, privacy protection and responsibly managing security risks. In implementing ISO 27001, your organization can tailor its policies with legal requirements and ethical guidelines at the forefront to ensure that your ISMS supports broader governance objectives.
Aligning your company’s ISO 27001 policies with both legal requirements and ethical guidelines will demonstrate that your organization not only complies with regulatory standards but also operates responsibly, protecting the interests of customers, employees, and stakeholders. While legal requirements provide a baseline of what must be done, ethical guidelines encourage organizations to go further, prioritizing privacy, transparency, and the fair treatment of individuals.
Identify the Legal Requirements you Must Fulfill and Relevant Ethical Guidelines
Based on the data your company handles and where it is located, are you required to comply with any or more than one of the following standards?
- GDPR for data protection in the EU.
- HIPAA for healthcare data in the U.S.
- CCPA for consumer data privacy in California.
- SOX for financial records and corporate governance.
It is crucial to review the requirements of any laws or regulations your organization is beholden to in order to avoid the steep penalties and serious consequences of non-compliance.
For instance, GDPR and HIPAA mandate timely incident response and breach notification. If you need to comply with these laws, your incident management policies should include clear procedures for identifying, responding to, and notifying relevant parties about data breaches.
Ethical compliance involves respecting and adhering to laws, regulations, and standards relevant to information security and data privacy. As compliance is a key component of ISO 27001, Annex A.18 requires organizations to identify applicable legislation and align their policies and practices accordingly, supporting ethical obligations to follow legal standards.
Map Requirements and Guidelines to ISO 27001 Policies and Controls With these requirements and ethical principles in mind, your organization must map them to ISO 27001 controls and policies in order to identify areas that need specific attention in your ISMS. Due to the flexibility of ISO 27001, its Annex A controls can be directly mapped to legal requirements, ensuring compliance.
For example:
- A.18.1.4: Privacy and Protection of Personally Identifiable Information (PII) aligns with data privacy laws, such as GDPR and CCPA, by requiring policies and controls that protect personal data.
- A.16: Information Security Incident Management supports requirements for breach notification in regulations like GDPR and HIPAA, which require timely reporting of data breaches.
- A.9: Access Control aligns with legal requirements for restricting access to sensitive information, supporting compliance with information protection regulations that mandate limiting access to authorized personnel only.
These controls encourage compliance with data protection laws (like GDPR) that require ethical data processing.
Regularly Train Employees on Both Legal Obligations and Ethical Responsibilities
It is essential to regularly educate your company’s employees on both the legal requirements and the ethical principles that govern data protection and security practices at your organization. Training should cover compliance topics such as data privacy, breach reporting, and access control and also highlight ethical values like transparency, fairness, and accountability.
Developing role-specific training modules will help employees understand how legal and ethical standards apply to their particular roles. For example, finance or HR teams may need more guidance on handling sensitive data with an added ethical focus on fairness and privacy.
Don’t forget to include real-world scenarios that demonstrate ethical decision-making in data security situations, reinforcing that employees should consider not only what is legally required but also what is fair and respectful to the individuals impacted by their actions.
You may also like: Why is Cyber Security Awareness Training Important for Employees?
Promote a Company Culture that Values Legal Compliance and Ethical Adherence
In addition to tailoring ISO 27001 policies to align with the governance objectives of your company, it is important to build a culture that supports the effective employment of these policies.
Encourage a security-first culture where both compliance and ethical practices are equally valued. Your company’s leadership should consistently communicate the importance of ethics alongside legal compliance in all security practices. By regularly and transparently communicating the legal requirements your organization must fulfill, you can head off security incidents that can occur when employees do not fully understand the stakes of handling stakeholder information and data.
Implement open feedback channels where employees can report or discuss potential ethical concerns or ambiguities in handling data securely and responsibly. Make it clear that ethical considerations are not secondary to legal compliance but are integral to your organization’s approach to information security.
While ISO 27001 provides a solid framework for securing information, aligning it with legal and ethical standards elevates your organization’s commitment to effective governance. By tailoring ISO 27001 policies to meet legal obligations like GDPR or HIPAA and embracing ethical principles such as transparency, fairness, and respect for privacy, your company will demonstrate a proactive approach to responsible data management that can appeal to potential clients and partners.
Regular training and fostering a culture that prioritizes both compliance and ethics solidify this commitment, which in turn reinforces your organization’s dedication to stakeholder trust and long-term security resilience. Ultimately, this integrated approach advances both regulatory adherence and corporate integrity, fostering a more robust governance framework.
Managing Policy Lifecycles
To ensure that your ISMS can rise to your company’s unique information security challenges, it is essential that your policies evolve over time. Policies are not static documents - they should be dynamic, changing to reflect your company’s goals, regulatory obligations, and values as they develop.
The lifecycle of your organization’s policies includes creation, review, approval, communication, and regular updates.
Here are best practices for managing the lifecycle of ISMS policies, which go hand in hand with updating, distributing, and training staff to implement policy controls:
1) Establishing a Policy Ownership and Governance Framework
As you create and enact ISMS policies, you must designate owners for each policy who will be responsible for overseeing updates, ensuring compliance, and answering questions. Once the policy owners have been established, then you need to define their roles and responsibilities with regards to the ISMS and the specific policies that they own.
2) Create a Centralized Policy Repository
Creating a policy management system, not only for ISO 27001 but other frameworks as well, is critically important when it comes to organizing and documenting company policies. A secure, centralized repository like a document management system (DMS) or governance, risk, and compliance (GRC) platform is the safest and most efficient way to store your ISMS policies. These platforms also allow you to save multiple versions of policies for documentation purposes so that you can track how they have changed over time. Your repository should allow employees and auditors easy access to the latest policies, with access restrictions for confidential or sensitive documents.
3) Implement a Consistent Update Procedure
Regular reviews should be scheduled, ideally annually, so that your organization can update outdated procedures consistently. Your operations and personnel are likely to change and evolve over time, but it’s also important to monitor changes to the laws and regulations with which you must remain compliant. A key part of the lifecycle management process is engaging stakeholders and personnel in relevant departments in order to ensure that the policies reflect the needs of the entire organization.
Lastly, the lifecycle of policy management should set out workflows for approving policy changes, typically involving the policy owner, legal, compliance, and senior management.
4) Enact Effective Policy Distribution and Communication
Using platforms like the company intranet, email notifications, or the DMS to distribute updated policies to staff is extremely important. In order to achieve compliance with several regulatory frameworks, companies must also implement mechanisms for employees to acknowledge they’ve read and understood policy updates, such as electronic signatures or quiz-based attestations. When major changes occur in the organization, your leadership must communicate them clearly, highlighting significant updates to avoid confusion.
5) Create Training and Awareness Programs
Having employees read and acknowledge that they’ve read your company’s relevant ISMS policies is often not enough to ensure that they will keep the recommendations and requirements outlined in the policies without more structure and training in place to support them. It is important to conduct regular training sessions that align with policy updates, focusing on key areas of data security, privacy, and compliance.
Another way to make sure that training is relevant and meaningful is to tailor training content to different roles. Technical staff may need in-depth sessions, while general employees might require broader security awareness training. Use interactive formats, such as e-learning modules, simulations, and quizzes to ensure employees understand and retain key policy points. Lastly, evaluate employees' understanding of the policies with assessments and adapt training as necessary based on results.
VIII. Understanding Stage 1 Audit & Readiness
Documentation Review
The first stage of the ISO 27001 Audit begins the two-stage external ISO 27001 certification process. The Stage 1 Audit consists of a comprehensive review of documentation by an external ISO 27001 auditor. The auditor will review your organization’s policies and procedures, verifying that they meet the requirements of the ISO 27001 standard and your company’s established ISMS.
In the Stage 1 Audit, the auditor will review the following:
- Information security policies and objectives
- Scope of the ISMS
- Risk assessment and risk treatment methodologies
- Statement of Applicability (SoA)
- Defined controls for information security
- Relevant procedures, records, and other essential ISMS documents
Readiness Assessment
In this first stage, the auditor also assesses the organization’s overall readiness for the Stage 2 Audit, including the adequacy of resources, commitment from top management, and employee awareness of the ISMS requirements. By identifying areas where documentation or processes may be incomplete or inadequate (nonconformities), the organization can address issues before the full certification audit, improving its chances of achieving certification.
Stage 1 Audit Readiness Checklist
As your team prepares for a Stage 1 Audit, you must verify that all essential elements of the ISMS are in place and align with the ISO 27001 requirements.
This checklist provides a structured approach to achieving readiness for the Stage 1 Audit, focusing on documentation, scope, and organizational readiness. Use this as a guide as you embark on your Stage 1 Audit.
1. ISMS Documentation
- Information Security Policy
- ISMS Scope Statement
- Information Security Objectives
- Risk Assessment Methodology
- Risk Treatment Plan Statement of Applicability (SoA)
- Information Security Policies and Procedures
- Control Implementation Evidence
- Records Management
2. Risk Management and Control Implementation
- Risk Assessment Report
- Risk Treatment Options
- Evidence of Control Implementation
- Evaluation of Risks and Controls
3. ISMS Scope and Boundaries
- Clear Definition of Scope
- Asset Inventory
- Stakeholder Identification
4. Organizational Readiness
- Top Management Commitment
- Roles and Responsibilities
- Competence and Training Records
- Awareness and Communication
5. ISMS Operational Procedures
- Access Control Procedures
- Asset Management Procedures
- Incident Management Procedures
- Business Continuity Plan (BCP)
- Third-Party Security
6. Monitoring, Measurement, and Review
- Internal Audit Program
- Management Review
- Corrective Actions
- Performance Metrics
7. Legal, Regulatory, and Contractual Requirements
- Legal Compliance Documentation
- Compliance Evidence
- Supplier and Contract Management
8. Initial Risk Treatment and Control Effectiveness Review
- Review of Risk Treatment
- Control Effectiveness Evaluation
- Documented Evidence of Risk Reduction
More Stage 1 Audit Tips:
- Run a Pre-Audit Mock Assessment: Conduct an internal “mock” audit to verify that documentation and processes are in place and catch any gaps before the actual audit.
- Organize Documentation for the Auditor: Make sure that all documentation related to your ISMS is well-organized and accessible for the auditor.
- Address Any Identified Gaps: If gaps are identified during the readiness assessment, address them before the Stage 1 Audit to avoid delaying the process.
Common Pitfalls to Avoid
It’s essential to go into the Audit 1 phase amply prepared. An auditor may delay conducting an audit for any of the following reasons:
- Incomplete documentation: Missing ISMS policies or procedures, incomplete risk treatment, or lack of a Statement of Applicability
- Undefined or unclear ISMS scope: Boundaries are ill-defined or nonexistent; scope lacks focus and clear goals.
- Lack of management commitment: No support from management or company leadership and insufficient resource allocation
- Unpreparedness for key ISMS requirements: Missing training and security awareness, lack of defined roles and responsibilities, insufficient risk management framework
- Inadequate internal audits or management review: Lack of a complete internal audit or management review is never scheduled
- Issues with document control or regulatory requirement: Lack of effective control implementation or undocumented controls
- Misalignment with legal and regulatory requirements: Overlooked legal requirements or evidence of non-compliance
- Inadequate preparation for audit logistics: Uncoordinated documentation access, unavailability of key personnel, disorganized documentation structure
- Inconsistent or insufficient incident management procedures: Lack of incident response plans or incident records
- Vendor and third-party compliance issues: Lack of third-party risk management or unverified third-party controls
Preparing for the Stage 1 ISO 27001 Audit is a critical step in achieving certification. By thoroughly reviewing documentation, addressing gaps, and aligning processes with ISO 27001 requirements, your organization will demonstrate readiness, minimize nonconformities, and pave the way for successful certification. A structured approach will facilitate a smooth and effective audit process.
IX. Understanding Stage 2 Audit & Readiness
As Stage 1 is mostly a document verification audit, you cannot ‘fail.’ However, you will receive recommendations for improvement or minor non-compliance, and you must present these recommendations to the auditor at the Stage 2 Audit. The waiting period between Stage 1 and Stage 2 is 90 days, providing you time to address and prepare anything noted by the Stage 1 auditor. However, if you do not present these documents in Stage 2, your organization will receive a major non-compliance and will not be recommended for certification.
An external accredited body performs the Stage 2 audit, or the certification audit, by collecting evidence of your ISMS in action, which is more than merely collecting documents as in Stage 1. The auditor will verify that your organization’s procedures and controls align with the requirements laid out in ISMS documentation. They also collect a wide range of data to ensure that the ISMS is operating correctly and interview key personnel in charge of managing the ISMS.
There are three main components of the Stage 2 Audit:
- Site Assessment: The auditor will either visit the organization's premises in person or are granted permission to the company's cameras to assess the actual implementation of the ISMS. They are given access to the organization’s security systems and documentation storage location.
- Risk Mitigation Evaluation: The auditor examines the organization's risk management procedures, assessing how identified risks are addressed and mitigated.
- Evidence Collection: Auditors gather evidence of the controls that have been implemented and how the ISMS conforms with ISO 27001 standards and legal obligations.
How to Know When You’re Ready for Stage 2
No two companies will be exactly the same in terms of readiness for the compliance audit. If you have evidence that you have implemented each necessary function of your ISMS along with any applicable Annex A controls, and have received and implemented feedback from a Stage 1 Audit, you are likely prepared to pass a Stage 2 Audit.
One sign that you are prepared for the Stage 2 Audit is that you have a handle on the basic requirements of ISO 27001:
Risk Management
- You have identified and documented all possible risks in your ISMS.
- You have explained how you will address each risk in your risk treatment plan.
- You have recorded every applied control in your Statement of Applicability (SoA)
- You have conducted personnel trainings so that staff have familiarized themselves with their roles in the organization’s risk management plan.
- You have logs, screenshots, and reports that prove that your controls are implemented correctly and are functioning as intended.
- You have implemented periodic reviews of your risk treatment plan and document each review/update.
Asset Management
- Your information asset inventory is comprehensive and includes not only software and hardware, but contracts with clients and vendors and other intangible assets like your brand/reputation.
- You have double-checked the asset inventory list and can explain to your auditor exactly which assets you are trying to protect with your ISMS.
- Each asset is assigned to an owner, ensuring accountability.
- Your assets are classified based on sensitivity and significance.
- You can demonstrate the access control procedures that keep your assets secure and can list every personnel member/account that has access to a given asset.
Incident Management
- You can demonstrate that your ISMS works in action because you and your team know exactly what to do in the event of a security incident.
- Your IRP is fully documented, including roles, responsibilities, and workflows.
- You have complete and up-to-date incident logs that the auditor can review.
- Your procedures for collecting and preserving evidence comply with legal requirements.
- You have nailed down a process for documenting lessons learned and regularly training personnel.
- You have conducted one or more incident drills so that you can assess how your IRP works in action.
Finding an Accredited Auditor
In order to achieve ISO 27001 certification, your organization will need to be audited by a certification body that thas been accredited by an accreditation body. The primary accreditation bodies in the United States are:
- ANAB (ANSI National Accreditation Board)
- IAS (International Accreditation Service)
- UAF (United Accreditation Foundation)
When you begin the ISO 27001 audit process, visit the websites of these accreditation bodies to access their directories of accredited certification bodies. ANAB provides a directory where you can search for accredited CBs by standard and location.
BD Emerson partners with Mastermind, a certification body accredited by the IAS for the assessment of management systems. Together, BD Emerson and Mastermind can facilitate your company’s path to ISO 27001 certification. BD Emerson’s team of skilled cybersecurity and privacy protection experts can guide your business through the implementation of ISO 27001 standards and its essential technical controls. Once your organization is prepared, we’ll provide a seamless handoff of your management system to Mastermind’s team of lead auditors for the necessary certification body audit.
What the Auditor Looks for:
Thorough and Accurate Documentation
In the Stage 2 Audit, you will need to provide all of the documentation of your ISMS as you did during the Stage 1 Audit, including:
- Risk Assessment Reports
- Risk Treatment Plans
- Control Documentation
- Incident Records
- Monitoring Logs
Satisfactory Interviews with Personnel and Key Stakeholders
The auditor will most likely need to interview the following stakeholders:
- Senior Management - As required by clause 5.1, auditors will interview senior management to ensure that they are committed to the ISMS and information security in general
- Risk Owners - Anyone identified as a ‘risk owner’ may be asked by an auditor how they assess risks, what their responsibilities are, and how they participate in implementing risk treatment plans.
- IT and Security Teams - The auditor will need to speak to your IT and/or information security team to verify how controls, such as network security, access management, and incident response are implemented.
- General Employees (often randomly selected) - Employees may be interviewed so that the auditor can evaluate their awareness of information security policies, their role in risk management, and their ability to identify and report security incidents.
Confirmation of Applied Technical and Operational Controls
During the Stage 2 Audit, auditors will dig for evidence that your technical and operational controls exist and are up to scratch. To do this, They will need the following key evidence:
- Access control lists and user access reviews
- Change management and configuration management records
- Encryption certificates and documentation of encryption standards
- Logs from SIEM systems, IDS/IPS tools, and other security monitoring solutions
- Results of vulnerability scans, penetration tests, and audit reports
- Records of security management training sessions and employee certifications
Tips for A Successful Stage 2 Audit
1. Prepare Thoroughly Before the Audit
- Don’t skip performing an internal audit or a Stage 1 Audit; they are crucial in getting your audit materials organized and identifying areas of focus for the auditor.
- Organize a pre-audit meeting so that you can brief your team on their roles, responsibilities, and the audit schedule.
- Have all relevant documents, policies, and evidence readily available. This includes your Statement of Applicability (SoA), risk assessments, incident logs, technical control documentation, and any documentation from your Stage 1 Audit
2. Have a Positive and Cooperative Attitude
- Be transparent about known weaknesses or areas of improvement in your ISMS. Transparency with the auditor can prevent minor issues from becoming significant findings.
- Be responsive when the auditor requests information or evidence and provide it promptly. Delays or evasion can raise red flags.
- Respect the auditor’s role and treat the audit like a cooperative process. The auditor is not trying to get you into trouble - they want to ensure that your ISMS meets the ISO 27001 standard.
3. Designate Someone as a Single Point of Contact
- Make sure to assign an audit coordinator to act as the primary contact person for the auditors. They should be either a compliance officer or the manager of your ISMS who is well-versed in your ISMS and can quickly respond to auditor questions.
- The audit coordinator acts as a needed liaison between the auditors and your organization, helping to avoid miscommunication. They make sure that requests are fulfilled efficiently and prevent the audit team from being overwhelmed with ad-hoc requests.
4. Schedule the Audit for When Key Stakeholders are Available
- Verify that critical team members are available to answer questions and sit down in an interview with the auditor to discuss their roles and responsibilities in implementing and maintaining controls.
- Prepare stakeholders that may be interviewed for potential questions and role-based demonstrations of how to implement ISO 27001 controls like access management, incident response, and data backup procedures.
5. Be Prepared to Demonstrate Controls in Action
- In the Stage 2 Audit, it is critical to show auditors not just documentation but controls in action, performing as intended. Be prepared to demonstrate the following controls in action:
a) Demonstrate technical controls such as access restrictions, encryption settings, and monitoring dashboards.
b) Show evidence of regular security reviews, incident logs, and vulnerability scans.
c) Walk auditors through physical security measures (e.g., secure access to server rooms, CCTV footage).
6. Anticipate Areas of Focus
Auditors will expect thorough evidence for the following high-risk areas:
- Access control
- Data encryption
- Incident management
- Vulnerability management
A lack of preparation in these areas can cause delays in the audit and even non-compliance.
7. Be Prepared for the Auditor to Use Sampling Methods
It is critically important to make sure that ISMS procedures are well-documented and universally followed so that any sample taken by the auditor will reflect compliance. Double and triple-check that records are complete and that recent logs, configurations, and audit trails are accessible to the auditor.
8. Maintain a Positive Audit Environment
- It is important to be cooperative and welcoming to auditors. Make sure they have access to necessary facilities, such as meeting rooms and internet access. Encourage your team to welcome the auditors and provide whatever the auditor needs.
- Do your best to minimize distractions by scheduling the audit during a period of relatively low business activity. This will allow staff to focus on responding to auditor requests and lessen stress around the audit.
9. As Always, Document Everything
- Make sure to keep a detailed record of the audit process, including questions asked, evidence provided, and any feedback the auditor gives. This documentation will be valuable for follow-up actions and future audits.
- If the auditor identifies non-conformities or areas for improvement, you should record their recommendations and start working on corrective actions immediately.
10. Conduct a Post-Audit Review
- After the audit concludes, hold a debrief meeting with your team to discuss the audit findings and lessons learned.
- Formulate a corrective action plan for any non-conformities or observations. Addressing issues promptly can prevent them from escalating in subsequent audits.
Main Takeaways:
- Be prepared: Thorough preparation can prevent delays and minimize findings.
- Be responsive: Quickly fulfilling evidence requests shows your ISMS is well-managed.
- Be transparent: Honesty about weaknesses can help foster a positive relationship with the auditor.
- Be consistent: Make sure that controls are consistently applied across the organization.
Following these best practices will help demonstrate that your ISMS is robust, effectively implemented, and capable of meeting the rigorous standards set by ISO 27001.
Post-Stage 2 Audit Actions
Though you’ve completed the Stage 2 Audit process, your work is not yet done! Once the certification audit is complete and the auditor has provided a report, it’s time to 1) Review the report’s recommendations, 2) Create a corrective action plan, 3) Provide evidence of correction and remediation, 4) Share your certification, and 5) Start preparing for the next recertification audit.
Step 1: Review Recommendation Status
At the end of the audit, the auditor will summarize their findings and the outcome of the audit by assigning you a status:
- Recommended: The auditor did not discover any non-conformities and recommends your organization for ISO 27001 certification.
- Recommended after Action Plan is Developed: A few minor non-conformities were identified, but with some corrective actions, the auditor believes these compliance gaps can be eliminated.
- Not recommended: The non-conformities discovered are too significant for your organization to address without a complete transformation of the ISMS and its security controls
Step 2: Review Non-Conformities (unless Recommended Status has been obtained)
The auditor will furnish a report explaining the non-conformities found and suggesting corrective actions. If possible, it is a good idea to plan a final meeting with your auditor to ask any last questions and get their input on the audit findings.
The first step of reviewing the non-conformities identified by the auditor is to determine their severity. There are a few categories of non-conformity:
Major Non-Conformity: Though not ideal, having a major non-conformity is not the end of the world. The auditor will label something as a major non-conformity if they cannot identify risk mitigation procedures that map to ISO 27001 standards.
Minor Non-Conformity: This type of non-conformity means that the auditor has confirmed that an ISO 27001-specific risk mitigation procedure exists, but it is not effective or is improperly executed. This level of severity will not impact your potential for ISO 27001 certification, but several minor non-conformities can lead to a major non-conformity.
Opportunity for Improvement (OFI): This category identifies areas where the efficiency of your organization’s ISMS can be improved. While recommended, addressing OFIs is not required for certification. However, implementing OFI recommendations will increase your odds of passing your next certification renewal.
Step 3: Addressing Non-conformities
Immediately following the audit, you will need to address the non-conformities found. If there is the possibility of rectifying a non-conformity, the auditor will label it as “open,” which means that there are steps you can take to correct the non-conformity. If the auditor labels a non-conformity as “closed,” on the other hand, that means they have accepted the corrective actions you have taken.
If the auditor identified non-conformities, you must:
1. Provide a Corrective Action Plan to the certification body within 14 days of receiving the nonconformity report.
The Corrective Action Plan must outline how your organization plans to address each non-conformity, who will be responsible for performing the actions, and how they will be implemented.
2. Give Proof of Correction to the certification body within 30 days.
You also have to provide evidence that you have corrected the non-conformities and that all actions laid out in the Corrective Action Plan have been implemented.
3. Provide Evidence of Remediation
For minor non-conformities, you must provide evidence of remediation before the conclusion of the post-audit review. For major non-conformities, you have until 60 days after the review ends to submit evidence of remediation.
For each non-conformity or OFI, you should keep a record of the following information:
- What occurred
- The actions that were taken to contain and mitigate any negative consequences
- The root cause of the event (if identified)
- Actions taken to eliminate the root cause (if deemed necessary)
- An assessment of the effectiveness of any action taken
Step 4: Create a Corrective Action Plan
Clause 10.1 offers a framework to model your Corrective Action Plan when addressing non-conformities.
The Corrective Action process will look something like this:
- Identify the non-conformity
- Log the non-conformity in the corrective actions log
- Assign responsibility
- Root cause analysis
- Determine a corrective action plan
- Implement corrective actions
- Monitor and review implementation
- Evaluate the effectiveness and impact of the corrective action
- Close the corrective action
- Document and report
NOTE: You may not have sufficient resources to undertake a root cause analysis for every non-conformity found. It’s important to prioritize your efforts and first complete a risk assessment for each non-conformity, and then pursue a root cause analysis for those that are medium or high risk.
Here is an example of what should be included in a Corrective Action Plan:
Step 5: Provide Evidence of Correction
Once you complete corrective actions, you will need to provide evidence for each non-conformity that you have rectified. Before committing to any corrective action, your team should evaluate how the change may impact your security posture
Some examples of evidence are:
- Screenshots: Visual proof of configurations, updates, or system settings.
- Meeting Minutes: Documentation of meetings where non-conformities and corrective actions were discussed.
- Emails: Communications confirming that changes were made or approvals were granted.
- Change Control Records: Evidence of changes being logged, reviewed, and approved by appropriate stakeholders.
Tips on Providing Evidence of Correction
It is important to be as thorough and detailed as possible in your evidence of corrective actions. A few general best practices are:
- Be Specific: Ensure the evidence directly addresses the identified non-conformity.
- Provide Clear Documentation: Include timestamps, signatures, or version control to demonstrate authenticity.
- Organize Evidence Logically: Use a checklist or table to link evidence items to specific non-conformities.
- Include Before-and-After Examples: Show the state before the corrective action was taken and the improvement of the state afterward.
Step 6: Provide Evidence of Remediation
For major non-conformities, you must provide evidence of your remediation actions to address each identified root cause. Your Remediation Action Plan will be almost identical in format to your Corrective Action Plan, but it will center on the immediate actions that have been taken to mitigate the risks and impacts caused by a non-conformity and in response to the findings of the root cause analysis performed.
Collecting and providing evidence of Remediation Actions within the 60-day window requires an efficient remediation management process. Start by clearly identifying the issue, assessing its impact, and defining objectives. Then, assemble a capable team and assign clear roles and responsibilities to each member. Prioritize tasks based on risk level and allocate necessary resources. For complex problems, use a phased approach to ensure systematic resolution.
After implementing remediation actions, verify their effectiveness through thorough testing and continuous monitoring to ensure issues are fully resolved. Document each step, including actions taken, assigned personnel, and results, for compliance and future reference. Collect evidence of the remediation actions at work in the form of screenshots, emails, and change control records.
Once all actions are completed, update policies and controls to prevent recurrence of similar issues. Don’t forget to use automation tools for vulnerability scanning and task tracking to increase efficiency, focusing on quick wins to minimize immediate risks and demonstrate your commitment to remediation to the accreditation body or auditor.
X. Surveillance Audits Post-Certification
What are Surveillance Audits?
Though you’ve achieved ISO 27001 certification, passing the Stage 2 Audit isn’t the end of the road if you plan to maintain compliance with the ISO 27001 framework. These recurring audits must be performed by a certification body periodically. They verify that your ISMS is still functioning properly and maintains ISO 27001 compliance but are less extensive than the initial certification audit.
How Often Do Surveillance Audits Occur?
After you become ISO 27001 certified, your organization’s certification lasts for a three-year cycle.
A surveillance audit will occur on an annual basis following the initial certification, so the cycle will look something like this:
Year 1: Initial certification audit
Year 2: First surveillance audit
Year 3: Second surveillance audit
Year 4: Recertification audit (to renew certification) After the third year, a more comprehensive recertification audit is required to renew the ISO 27001 certification for another three-year cycle.
What is Reviewed during a Surveillance Audit?
Surveillance audits focus on specific areas of the ISMS, such as high-risk areas identified in previous audits, changes in the organization, or new threats that have emerged. The scope is usually more limited than the initial certification audit but still comprehensive enough to assess critical aspects of the ISMS.
Surveillance audits usually evaluate:
- Management team commitment
- Key process performance
- Risk management and mitigation processes
- Internal audit practices
- Areas of non-compliance
- Areas of concern
- Documentation and records
- Suggestion implementation following the first audit
It is extremely important to keep all of the records and documentation from prior audits so that the auditors can trace your organization’s implementation of the ISMS, enabling the recertification audits to run smoothly.
Tips on Preparing for Surveillance Audits
There are no clear guidelines to follow when it comes to preparing for a surveillance audit, but here is a helpful checklist of actions you can complete to increase the likelihood that you succeed in each surveillance audit.

1. Prepare an Audit Agenda
You should have an audit agenda from your Stage 2 certification audit, but it helps to create your own if you do not.
The agenda may include the following items:
- Opening Meeting
- Review of Previous Audit Findings
- Review of ISMS Documentation
- Risk Assessment and Risk Treatment Plan Review
- Testing of Key Controls
- Incident Management and Security Monitoring Review
- Verification of Compliance with Legal, Regulatory, and Contractual Requirements
- Stakeholder Interviews
- Site Visit (if applicable) for Physical Security Review
- Continuous Improvement / OFI Review
- Concluding Meeting
Determine with the auditor when and how these reviews will take place, and make sure your team and any relevant employees are aware of the audit and how it may affect day-to-day operations while in progress.
2. Conduct an Internal Audit
As you did for your first internal audit, create a checklist of all necessary documentation, evidence, and processes to review before the surveillance audit. Use the checklist to conduct a final internal audit a few weeks before the surveillance audit to ensure nothing is overlooked and that you have ample time to address any non-conformities you may find before the surveillance audit takes place.
3. Create an Audit Schedule
Like the agenda, this schedule will organize the components of the audit into an easy-to-follow workflow. The schedule should, however, include where the auditor will be, or when they will interview staff and other stakeholders.
4. Communicate about the Audit to Your Employees
When it comes to following ISO 27001 best practices, maintaining transparent communications with your personnel is essential. Communicate to all employees when the audit will be taking place and the areas of your company that may be impacted. Encourage your employees to cooperate with the auditor to ensure efficiency.
5. Make Sure Records and Documentation are Up to Date
Do a sweep to make sure that management systems are up-to-date and that you have access credentials that the auditor may need on hand. Make sure you have important data ready to pull when the auditor needs it so that you can keep the audit running smoothly. Make a list of any personnel or employees who may have departed or joined your organization so that you know exactly which personnel have had access to sensitive information and can furnish the auditor with that information.
6. Note Any Changes as a Result of Corrections
Have any corrections you’ve made to controls or processes changed impacted the scope of your ISMS? If so, you should verify that your controls and policies reflect these changes and still align with ISO 27001 standards.
7. Prepare Answers and Data
Your auditor will ask you a ton of questions, and it is important to not let these questions catch you off guard. You should have organized and prepared information at the ready so that you can answer questions accurately and easily find the information you are looking for. Make sure that you can explain exactly how your information security controls align with ISO standard requirements. Of course you don’t have to memorize that information, but you should know how to find it quickly within your records.
8. Use Each Audit to Prepare for the Next
Document the questions the auditor asks, areas where you might have been less than ideally prepared, and anything the auditor flagged as an area for improvement. Of course, if you have any non-conformities identified, you will need to record the corrective actions you take to address them. With this information, prepare a customized checklist for your next surveillance audit.
Strategies for Avoiding Compliance Drift or Complacency after ISO 27001 Certification
Create an Information Security First Culture
Having key leadership on board throughout the ISO 27001 certification process is critical to avoid slipping into non-compliance. Often, organizations without adequate leadership commitment and resource investment in their certifications lose compliance. With a diligent effort at integrating the ISMS into the business’s core objectives, and including personnel throughout the certification process/transparent team communication, you can work to ensure that your organization’s people value high standards of information security and understand its importance. This will allow the certification effort to remain cohesive and supported.
Make Sure Your Risk Assessments are As Thorough As Possible
The risk assessments performed as you integrate your ISMS and conduct the internal audit are critically important. Any underestimated risks or unidentified weakness could lead to a security incident that will in turn compromise your entire compliance effort. Sit down with the leaders of each department in order to get a thorough understanding of possible risks you are unaware of. Don’t rush through your risk assessments - treat them as ongoing processes and revisit risks and controls often.
Review Documentation to Verify that it is Complete and Consistent
Confirm that your procedures, policies, and records are consistent and clear. They should create a reliable framework that supports the functioning of your ISMS and allows your team to focus on upholding best practices relating to information security. Consistently reviewing and updating your documentation ensures alignment and provides your team with the necessary guidance to follow established procedures. Making the latest documents accessible to everyone promotes accountability, precision, and adherence to compliance standards across the organization.
Define the ISMS Scope Clearly
It is essential that your ISMS scope clearly includes all relevant information assets, departments, and processes. If the scope is not properly defined, critical areas may be overlooked, creating vulnerabilities and risking compliance failures.
This ambiguity can also lead to confusion among employees regarding what falls under your information security efforts and what doesn’t. If your team isn’t clear on the ISMS’s reach, it can result in inconsistent application and enforcement of security policies. To avoid this, collaborate with various departments to thoroughly assess their processes and information assets, ensuring that the scope is both comprehensive and appropriate.
Maintaining ISO 27001 compliance is not a one-time achievement but an ongoing commitment that requires continuous attention and effort. By fostering a culture where information security is prioritized, conducting thorough and iterative risk assessments, ensuring up-to-date and accessible documentation, and clearly defining the ISMS scope, your organization can prevent compliance drift and complacency.
Consistent engagement, leadership support, and a proactive approach to risk management will help your ISMS remain robust and aligned with your organization’s evolving needs. In doing so, you not only protect your information assets but also strengthen trust with stakeholders by demonstrating a deep commitment to high information security standards.
Summary
If you decide to pursue ISO 27001 certification, revisit this comprehensive guide as you define the scope of your ISMS, build out your risk management system, conduct internal audits, plan management reviews, implement controls, and prepare for certification and surveillance audits. Maintaining ISO 27001 certification is not a one-time achievement – it requires continual improvement and evolution. The digital world is always changing, and your ISMS has to change with it in order to remain effective and compliant.
Ready to Pursue ISO 27001 Certification?
If you’d like to learn more about ISO 27001 certification and how BD Emerson can support your team through the process, schedule a consultation with our experts.











